We would love to see more quality press attention to the issue of WordPress plugin security because there certainly is much discuss, unfortunately, as with security journalism in general, when it does get discussed these days the reporting is mostly awful. Take for instance the Ars Technica article More than 1 million WordPress websites imperiled by critical plugin bug (written by the same person who last year wrote an article that we found to be completely baseless).
The words imperiled and critical are probably not appropriate, considering that the vulnerability in WP Slimstat was fixed in an update last week (you can turn of WordPress ability to automatically updates plugins with one of our plugins) and due to the type of vulnerability. The vulnerability is a blind SQL injection vulnerability, which can allow data to be read out of the database. While this has the potential to be rather serious if you store sensitive data on the website, this type of vulnerability isn’t often exploited by hackers that are not targeting specific websites (most hacks are not targeted). So the chances of it being exploited are rather small in comparison to say a vulnerability that allows PHP files to be uploaded to a website, which we can almost guarantee is going to be exploited, most likely sooner rather than later. The chances of this plugins vulnerability being exploited are even slimmer because it requires a fair amount computing being done before you can exploit it, unlike plenty of other blind SQL injections that have been found in WordPress plugins.
The big problem with the article comes from the claim in the title that “more than 1 million WordPress websites imperiled”. Over a million websites impacted make this sounds like a major issue, the problem is that it isn’t close to being true. If you read through the article nothing is provided that backs that number up, instead only the download count of the plugin is mentioned:
WP-Slimstat is an analytics tool. Its listing on WordPress shows it has been downloaded more than 1.3 million times. People who operate websites that use the plugin should update immediately.
Downloads of software obviously are not the same as how many websites are using software, so treating them the same is something a journalist concerned about accuracy wouldn’t be doing. But what makes it so bad for WordPress plugins is that each time a plugin gets updated through the WordPress admin area that counts as new download, so the actual user count is going to be much smaller than the download count, especially if the plugin is updated frequently. The download graph for one of our plugins dramatically shows how updates impact the download count:
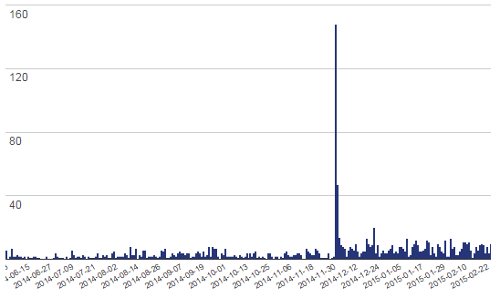
You see that huge spike that on the graph, that is when we updated the plugin. On that day there were 148 downloads and the next day there 47 the next day. That compares to 9 downloads a day we averaged over the last week. Those two days work out to 13 percent of total downloads so far.
WP Slimstat is updated more often so there are lots of spikes on the graph, of which, most if not all are due to updates:
Ars Technica isn’t alone in this, a quick search pulled up more articles on this vulnerability with the same highly inflated website use count:
- Help Net Security: Over a million WP sites at risk of hijacking due to plugin bug
- ITProPortal: CRitical bug puts millions of WordPress sites in danger
- PCWorld: Million-plus WordPress sites may be vulnerable due to flaw in popular plug-in
- Threatpost: More than 1 Million WordPress Sites Open to SQL Injection Attacks
- ZDNet: Over 1 million WordPress websites at risk from SQL injection
It also worth mentioning that this type of article has the potential to be somewhat harmful to security since you need to being keeping your WordPress plugins update to date all the time instead of trying to be on the lookout for mentions of fixed security issues since security fixes often are not even mentioned in plugins’ changelogs.
