When it comes to security companies, trustworthiness is critical, since the average person isn’t going to have the knowledge and skills to understand if the security company is actually doing (or could even possibly do) what they are claiming to do to protect them. Any upstanding security company would therefore be very careful in what they say and do, so if you see a company being less than honest it should be a major red flag when it comes to using their products and services.
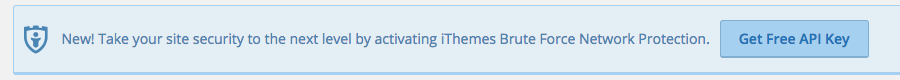
That brings us to something we noticed in the WordPress security plugin iThemes Security. When you install the plugin a notice is displayed at the top of pages in the admin area that read “New! Take your site security to the next level by activating iThemes Brute Force Network Protection”
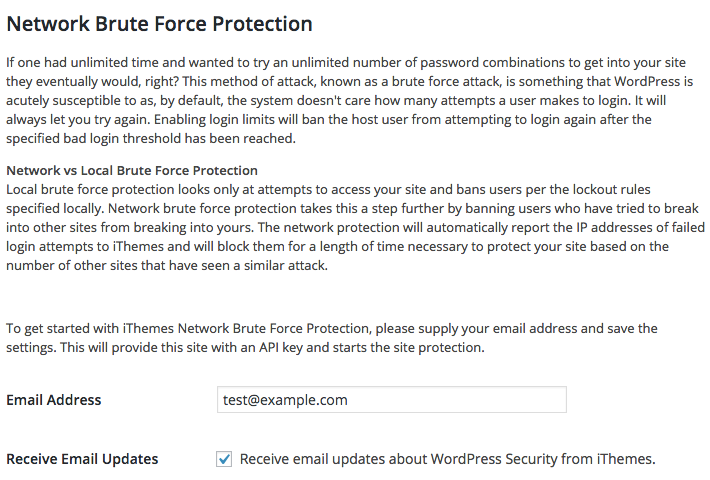
If you get click the “Get Free API Key” button in that notice you get shown the following page:
On that page they accurately describe what a brute force attack is, so clearly they know what it is. What they either don’t know or they are intentionally not telling people is that brute force attacks against WordPress admin passwords are not happening, so you are not taking your site security to the next level by enabling that feature as they claim.
What makes this more troubling is that they are using the non-existent threat of brute force attacks to try to collect users’ email addresses. By default permission to send “email updates about WordPress Security” is also included when doing that and considering in the best case here they are not aware of it pretty basic security fact that brute force attacks are not happening, the quality of the security information they would provide in those email is likely to be poor.
Just based on this it would seem like a good idea to avoid this company and their plugin, but it isn’t the only issue we found with the plugin recently. Back in April we ran across the fact that the plugin had button labeled “One-Click Secure” that didn’t do anything.
This post sounds like it’s saying “iThemes are conning you” but actually what you’re saying (much as in the “Brute force attacks are not happening” post) is that iThemes are conflating “brute force” and “dictionary” attacks. So your clickbait overstatement headline is misleading – using the terms wrongly is not helpful but it’s hardly a major transgression, since iThemes protects against both. To anyone who understands this it makes you look decidedly untrustworthy yourselves, but to many people these claims will cause needless alarm.
You don’t provide anything to substantiate your claim that iThemes is harvesting email addresses, but I can’t refute your point because I simply can’t understand the meaning of the penultimate paragraph in this article – the grammar is just too mangled.
I use iThemes but have no affiliation with it. I’m only posting this because this comes up quite high in Google for “network brute force ithemes” related searches and it’s not helpful.
If you read the post, you would see that we explain that iThemes correctly explains what brute force attacks are, so they are not conflating anything, they are just falsely claiming they something is happening that isn’t. That is accurately reflected in the title of our post. It is unfortunate that you are trying to mislead people about what is really going on here and claiming that we look untrustworthy when you are the one trying to mislead people here.
The proper way to protect against dictionary attacks is to use a strong password, which doesn’t require any plugin.
Also, if you bothered to read the post you would see that they are collecting people email addresses when people sign up a free API key for the network brute force protection. That is shown right in the second image in the post.