When it comes to security companies we often say that they many of them don’t know and or care about security, which we think explains a lot of why security is in such bad shape these days. One example that we often find of this is that these companies are failing do the basics when it comes to the security of their own websites. We recently looked at one cyber security company that claims to have “clients in the intelligence community, DoD and nearly every cabinet agency” and isn’t bothering to keep the software running the various parts of their website up to date while telling the public they need to take advanced measure to protect their websites. They are not the only cyber security that has failed to that.
CrowdStrike was recently in the news due to their investigating the security breach at the Democratic National Committee (DNC) and placing the blame for it on the Russia government. They offer a variety of products and services intended prevent security breaches and respond after them. They also happen to be running an outdated and insecure version of WordPress on the main portion of their website:
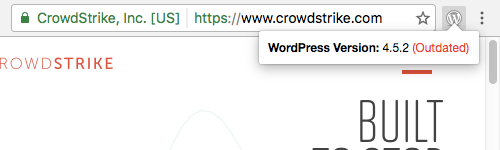
The blog section of their website is running an even older version:

Like the previous case what makes is particularly troubling is that they are not just running an outdated major version of WordPress, version 4.6 was released in August, but they are not running the latest version of 4.5, 4.5.4. That isn’t normal, as back in WordPress 3.7 a new update system was introduced so that minor updates normally happen automatically. So either CrowdStrike disabled those automatic updates (which isn’t a good idea) and then failed to apply the updates manually or their is some incompatibility between their hosting environment and the update system and they also failed to apply the updates manually. If it was the later, then they could actually help improve security by working with the WordPress developers fix whatever is causing those automatic updates to no happen.
Whichever is the case, the end result is that they have multiple known vulnerabilities on their website, as WordPress 4.5.2, 4.5.3, and 4.5.4 all included security updates.
The next question is whether this an aberration or if this is indicative of larger problems with handling and understanding of security at the company, which is something that companies looking to use their products and services or journalist looking to cite them should probably find out.
Hi, the blog needs to be corrected please. The information is based on html meta-tags and should not be used as the only means for determining if a site is vulnerable.
Our site is actually a static page and read only. It’s not running on WordPress on the Internet site but we do use it to generate content. What you’re alluding to is not correct.
Happy to discuss further and will send an email to your contact address.
Again, most vulnerability teams would not rely on meta-data alone. That almost never tells the full story of whether a site is at risk or not.
Jerry
Crowdstrike CISO
Your blog doesn’t have a WordPress meta generator tag, so that couldn’t have been used to determine the version in use there. You also are not denying that you are using outdated versions of WordPress, instead trying to obfuscate away from that issue.
Static files can have vulnerabilities in JavaScript code for example, so even static files could put people at risk. Not to mention that someone who knows the internal address of intranet accessible WordPress installation can leverage a vulnerability in it to gain further access to a companies systems (you should understand that based on what services you provide).
It also turns out the WordPress installations are not the only issue, your Drupal installation at https://intel.crowdstrike.com even more out of date as it is running either Drupal 7.12 or 7.13, which puts it over four years out of date.