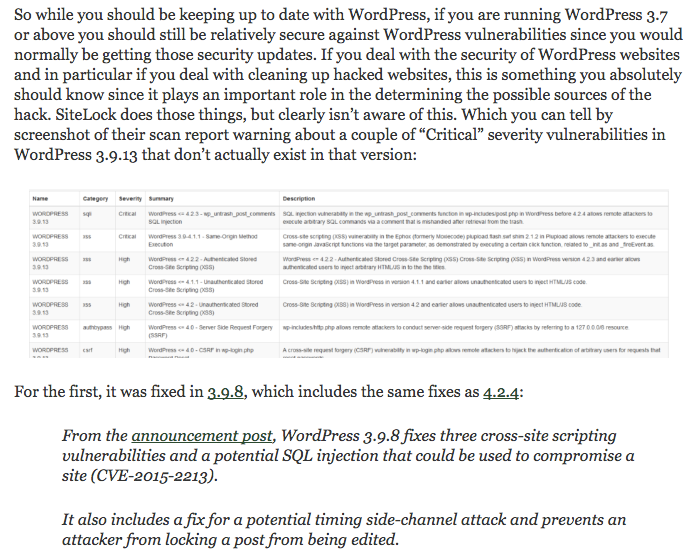
Earlier this week we discussed a situation where a couple of articles on tech news websites labeled several vulnerabilities disclosed in a Dell EMC product as being zero-day vulnerabilites despite there being no indication that was the case. A zero-day vulnerability is a vulnerability that is exploited before the developer is aware of the vulnerability. That obviously is serious situation since you have a vulnerability that is being exploited and having kept your software up to date will not protect you against exploitation. As we discussed in more detail in that previous post, security companies and the press often label vulnerabilites that are not zero-day vulnerabilities as being them, which is not helpful in trying to understand the threat landscape. Our best guess was that the claim that these were zero-day vulnerabilites was included in those articles due to a press release from the discoverer of the vulnerabilites referring to them as being zero-day vulnerabilites (without any supporting evidence), as the discoverer’s post on the issue didn’t not make any reference to them being zero-days.
In the previous post we mentioned that one of the articles came from ZDNet, but more specifically it came from their blog Zero Day. It would be a pretty telling example of how bad security journalism is if they didn’t even understand what the namesake of their blog actually means. But making that assumption on one wrong article would be unfair, so we started taking a look to see if this had happened before and it clearly wasn’t a one time fluke.
We just had to go back to the 3rd to find another example, this time OpenJPEG zero-day flaw leads to remote code execution. The last two paragraphs make it clear this wasn’t a zero-day vulnerability:
The vulnerability was discovered by Aleksander Nikolic from the Cisco Talos security team in OpenJpeg openjp2 version 2.1.1.
Cisco Talos disclosed the vulnerability to affected vendors on 26 July, granting them time to prepare patches to fix the problem before public release.
So the vulnerability was discovered by a researcher, reported to the developers, and fixed before public release. There is no indication in the article or advisory that it has ever been exploited.
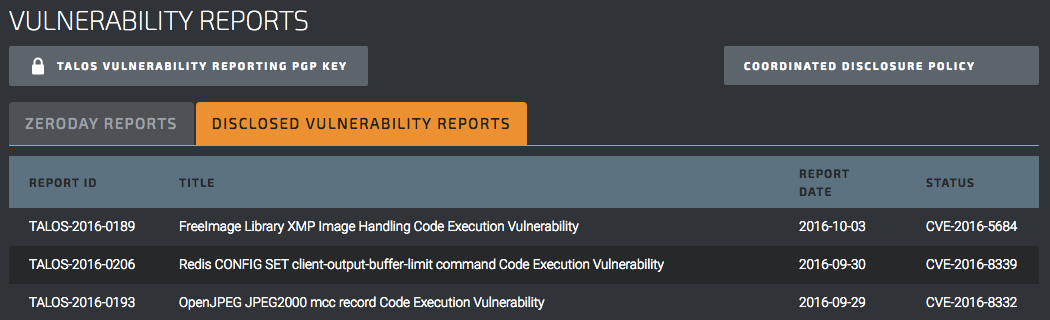
The discover also breaks down their vulnerability reports as Zeroday Reports and Disclosed Vulnerability Reports and you can see that this issue is listed as being the latter:
Heading back a few weeks we found the article Zero-day vulnerability found within MySQL database application. In this case the vulnerability was reported to the developer before it was disclosed:
On Monday, independent security researcher Dawid Golunski released his findings through a public security disclosure, stating that over 40 days have passed since the zero-day vulnerability was reported to the vendor.
Nothing in the article or the linked public security disclosure provides any indication it was being exploited before the developer was notified, so it is not a zero-day.