Three years ago we posted about the fact that trust marks shown on websites that claim to certify that the websites are secure cannot be trusted to identify if a website is actually secure for a number of reasons, including that in many cases they scan the websites from the outside so there are many things that they would never detect. What we recently noticed is that the Norton Secure Seal service fails to do a really basic security check that can be done from the outside. When it comes to the security of websites one of the basic security measures is to keep the software running the website up to date. This prevents the website from being hacked to the exploitation of a known vulnerability in the software that has been fixed in a subsequent release. As we have found the Norton Secure Seal service doesn’t check to make sure the software running the website they are claiming is secure is up to date.
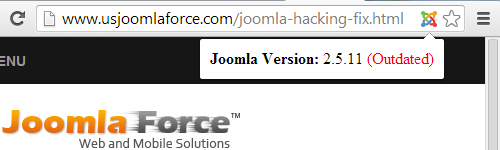
As an example of this we will take a look at the website of an IT security company that carries the Norton Secure Seal as you can see here:

Using our Joomla Version Check web browser extension you can see that the website is running an outdated version of Joomla:
 That version of Joomla, 3.1.1, is seven months out of date and more importantly subsequent versions have fixed four security vulnerabilities, including a vulnerability rated as having critical severity and a vulnerability rated as having high severity. A website with that level of security issue should not be labeled as being secure.
That version of Joomla, 3.1.1, is seven months out of date and more importantly subsequent versions have fixed four security vulnerabilities, including a vulnerability rated as having critical severity and a vulnerability rated as having high severity. A website with that level of security issue should not be labeled as being secure.
The technology our web browser extension uses to detect that Joomla is powering a web page and what version is in use is rather simple and there is no excuse for a major company such as Symantec, the maker of the Norton Secured Seal service, not being able to do the same. Providing more awareness that an outdated version of Joomla is in use is definitely needed as outdated versions of Joomla are widely used, including among companies that provide security services for Joomla websites, and some older versions contain a vulnerability that is being exploited by hackers.
It isn’t just Joomla that Norton Secured Seal service doesn’t check to make sure is up to date; the same website has a blog running an outdated and insecure version of WordPress as well: