On Tuesday we looked at example of the poor state of security journalism. In that case a hack was tied to a specific version of TYPO3, despite fact that websites not running that version of TYPO3 or running TYPO3 had been hacked. There was also the larger issue that no evidence was provided as to how the websites were hacked, which would have been what would be needed to actually tie the hack to a specific version of TYPO3 and would allow people to make sure the protected their websites against it. Just a few days later we have spotted another very similar example worth highlighting. Ars Technica today put out an article “Ancient Linux servers: The blighted slum houses of the Internet” that states:
Now comes word of a new mass compromise that preys on even more neglected Web severs, some running versions of the Linux operating system kernel first released in 2007. According to a blog post published late Thursday by researchers from Cisco, the people behind the attack appear to have identified a vulnerability that has since been patched in later Linux releases that allows them to dish malicious content to unsuspecting people who visit the site.
If you read Cisco’s blog though they only state “it is possible” that a “vulnerability that has since been patched in later Linux release” was the source of the hack, while Ars Technica says that it “appears” to be the case. Here is the relevant section of Cisco’s post:
Attackers compromised legitimate websites, inserting JavaScript that redirects visitors to other compromised websites. All of the affected web servers that we have examined use the Linux 2.6 kernel. Many of the affected servers are using Linux kernel versions first released in 2007 or earlier. It is possible that attackers have identified a vulnerability on the platform and have been able to take advantage of the fact that these are older systems that may not be continuously patched by administrators.
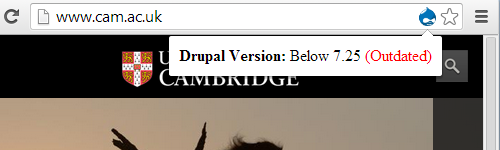
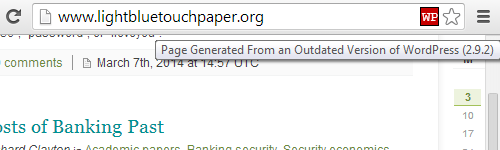
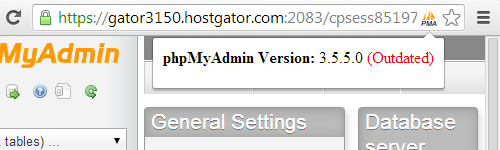
That turns out to be less of an issue then the fact that the websites are not even all running Linux, much less the Linux 2.6 Kernel. Some websites provide information on the software running the in HTTP headers served with the page. Our Server Details web browser extension, available for Chrome and Opera, can parse those HTTP headers to provide the details in them and warn for outdated software. Using those headers we started going through the Cisco’s list of compromised websites and second compromised websites. For each we have listed below the first five websites we found not running Linux and what operating system they are running:
Compromised Websites
archive.mrpools.co.uk Windows Server 2003
blueprintbowling.com Windows Server 2008 R2
hwy65mx.com Windows Server 2003
jandjpoolspa.com Windows Server 2003
mussotra.com Windows Server 2003
Second Compromised Websites
3d2print.eu FreeBSD
7va.cc Windows Server 2008 R2
babycaust.info Windows Server 2008
banderil.com.ar Windows Server 2008 R2
c2consultores.com.ar Windows Server 2008 R2
Cisco provides no evidence of how the websites were hacked, which is the really important thing to prevent more websites from being hacked. If they had actually determined how it was hacked before jumping to speculation then they wouldn’t have tried to connect this to Linux, which it seems pretty likely it doesn’t have anything to do with. Cisco also has provided no evidence this has anything to do with outdated software, if we were to make an educated guess based on the evidence provide so far we would say it is more likely due to compromised FTP credentials, which could easily be checked for by reviewing the FTP logs for the websites.
We should also note that the use of the Linux 2.6 kernel is does not indicate that website using obsolete software, as distributions including Debian, Ubuntu, and Red Hat still have supported releases that use that version of the Linux kernel.





 The version they are using is not just a little out date. Support for Apache HTTP Server 1.3
The version they are using is not just a little out date. Support for Apache HTTP Server 1.3