A week ago an authenticated SQL injection vulnerability and a cross-site scripting (XSS) vulnerability that exist in the latest version of Moodle was publicly disclosed. The post that was done in makes no mention of notifying the Moodle developers about the issue.
The vulnerabilities received more exposure in a article on a news outlet owned by the security company PortSwigger yesterday. Curiously, especially considering the owner of the news outlet, the post doesn’t address why the vulnerabilities appear to have been full disclosed, instead of being reported to developer first. That article does say that the author of it contacted Moodle:
The Daily Swig has reached out to Moodle to learn more and will update this article accordingly.
(That article also inaccurately states that the “bug appears to have been reported in a GitHub post from 2013”, when according the original post, that was when the vulnerabilities were introduced, not reported.)
So far the post hasn’t been updated with a response from Moodle.
We confirmed that the claims made about the authenticated SQL injection vulnerability and cross-site scripting (XSS) vulnerability are true with the most recent version of Moodle, 3.11.5. Based on when the vulnerabilities were introduced in to the code, they should also exist in the latest version of previous versions of Moodle that still receive security updates, 3.10.9 and 3.9.12.
To exploit this the attacker would need to be logged in to Moodle and be assigned to be a teacher of a course. The SQL injection vulnerability could be exploited to read the contents of Moodle’s database and the XSS vulnerability to cause malicious JavaScript code to be shown one pages on the website.
We contacted Moodle’s security team yesterday to make sure they were aware of this.
While we don’t know why the discloser appears not to have notified them, we found that the form they provide for reporting security issues problematic and could turn people away from reporting issue to them. As one example of that, the form includes several hard to understand items. Including one wanting to the know “Target”:
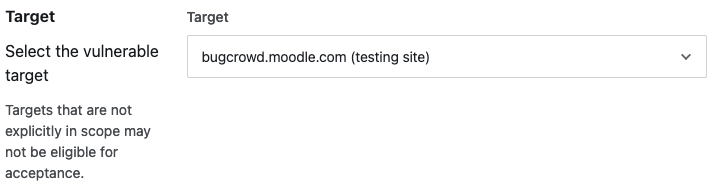
With the two options provided being “bugcrowd.moodle.com (testing site)” and “Other”. We are really in contact with developers about security issues in their software and we are not sure what that is supposed to refer to.
At the end of their form is a quite strange item for someone simply trying to report a security issue, you have agree to terms and conditions of a company named Bugcrowd:

It isn’t explained why you should be need to do that or why that third-party should be involved in trying to address something with Moodle.
We noted those issues when we notified Moodle and hopefully they will get things improved, so that people are more likely to report issues to them first instead of publicly disclosing them.
If you have a Moodle website that has been hacked, we offer a service to help address that.