Considering the poor state of security, better understanding where companies need to improve their security could be very useful. A big problem with doing that is how can you measure that. That appears to be a problem with a study released in December from Bitsight and Google. That is well summed up with this chart from the report listing how computer software companies did in handling various controls of the Minimum Viable Secure Product (MVSP) framework:
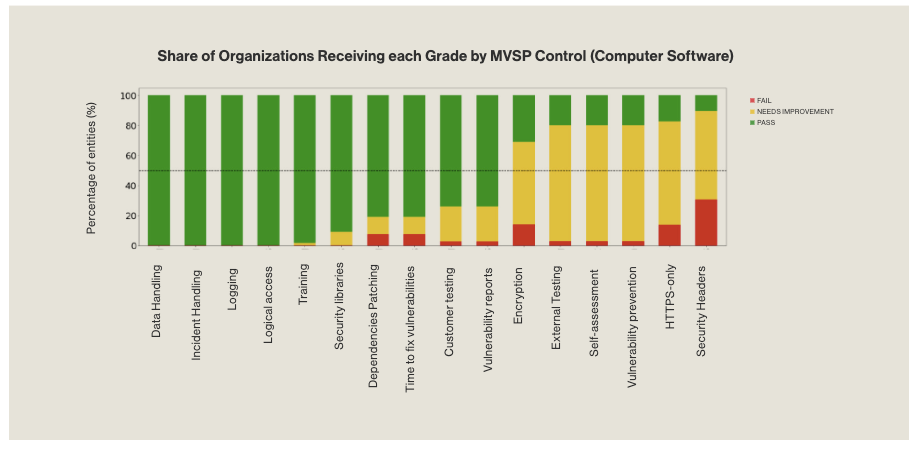 They did worst on security headers, which is additional data sent along with web pages by web servers to web browsers instructed them to do or not do things. That is something that is easy to measure since if the website is publicly available, anyone can check those in an automated way.
They did worst on security headers, which is additional data sent along with web pages by web servers to web browsers instructed them to do or not do things. That is something that is easy to measure since if the website is publicly available, anyone can check those in an automated way.
The controls where they did best are ones that seem hard to measure easily and from the outside. The study states that information for those controls comes from information that has “been publicly disclosed”:
Security Incidents and Data Breaches provide evidence
of security incidents that have been publicly disclosed
and insight into incident management practices.
That creates a huge blind spot, as anything that isn’t publicly disclosed wouldn’t be measured.
It seems reasonable to think that there is a correlation between doing better at measures with limited ability to measure and doing worse with measures that are easy to measure, based on the failure rates of the various controls.
Another problem with this approach is that security headers offer little security value, as attackers can simple ignore them. By comparison, data handling and incident handling are critical to security. Having a measurement system that is more accurate with much less important things could provide a rather skewed view of how well companies are handling security on an individual basis, but also in comparison to other companies.