Yesterday we discussed someone’s belief that their website would be useless in its current form due to a company’s blog post about Google making a change to their Chrome web browser to label non-HTTPS websites as “not secure”. Unrelated to that, yesterday we got sent an email from GoDaddy touting purchasing SSL certificates from them to avoid websites being labeled that way by Chrome. Two things stood out with that. The first being that GoDaddy charges much more than you need to be paying for an SSL certificate, which will in part prevent a website from being labeled as “not secure”, but also that GoDaddy doesn’t seem to really understand what they talking about when it comes to HTTPS. That latter fact isn’t all that surprising considering GoDaddy’s poor security track record.
The subject of the email was “Your customers need SSL on their sites ASAP.”.
On the page linked to from the email, their lowest end SSL certificate, which would be the level you need to avoid the “not secure” label, the introductory price is 60 dollars if you pay for two years upfront and then after that 75 dollars:
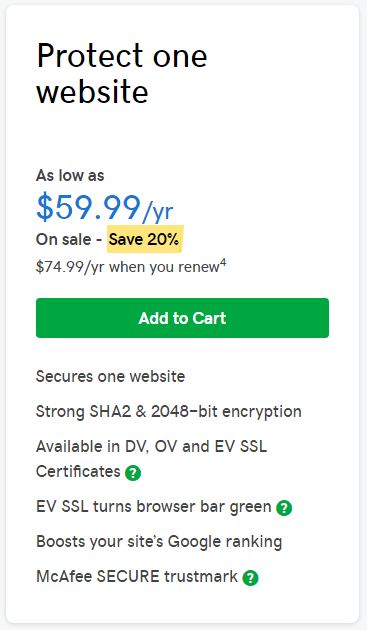
With other providers you can pay a fraction of that price. It also looks like that used to be true with GoDaddy as well, as they have apparently significantly increased the prices they charge for SSL certificates over the years despite nothing that would have increased their costs.
Using Let’s Encrypt you can even get a free SSL certificate and there are plenty of web hosting providers that have the capability integrated into their control panels to allow setting those up. It’s worth nothing that GoDaddy’s security company has been a major sponsor or donor to Let’s Encrypt, which seems like a tacit endorsement of Let’s Encrypt .
That GoDaddy is overcharging for SSL certificates instead of being like other hosting providers and offering free SSL certificates seems worse to us when reading one of the three testimonials they chose to show on that page that touts them providing an affordable solution:
I received a call from product support to let me know Google was getting more rigid about “secure sites”. We were able to make the upgrades that I could afford, and make my site more mobile accessible AND secure.
Another testimonial seems more insidious since it gives the impression that GoDaddy is providing cheaper certificates than others instead of more expensive ones:
I’ve set up SSL certificates from various companies but will never use anyone but GoDaddy every again. It’s easy to set up, great support and at a fraction of the price it’s great all around!
That is a great example of why testimonials are not a great source of information because that one allows GoDaddy to make it seem like they providing a more reasonable priced product without having to lie. If they really were providing cheaper certificates they would have been able to present evidence to back that up.
Misleading Marketing
The email made the following claim:
SSL is not only the right thing to do for your customers, it’s also great for boosting their search rankings and getting more traffic to their sites.
No link was provided that backed up that claim. On the page to purchase an SSL certificate, the claim is made repeatedly in regards to Google search results, but again no evidence is provided.
Based on what Google has said it doesn’t sound like using HTTPS has much impact. Here is in part what Google said when the disclosed that usage was a ranking factor:
We’ve seen positive results, so we’re starting to use HTTPS as a ranking signal. For now it’s only a very lightweight signal—affecting fewer than 1% of global queries, and carrying less weight than other signals such as high-quality content—while we give webmasters time to switch to HTTPS. But over time, we may decide to strengthen it, because we’d like to encourage all website owners to switch from HTTP to HTTPS to keep everyone safe on the web.
As far as we are aware they haven’t announced strengthening it and they seem to be using changes to Chrome to increase usage of HTTPS.
In another instance, a Google employee explained the impact as follows:
If you’re in a competitive niche, then it can give you an edge from Google’s point of view. With the HTTPS ranking boost, it acts more like a tiebreaker. For example, if all quality signals are equal for two results, then the one that is on HTTPS would get … or may get … the extra boost that is needed to trump the other result.
Importantly, if both websites were using HTTPS the impact on the ranking boost of either one would be nullified.
Misleading on that seems of less importance than a page they created just to promote buying their SSL certificates due to the change to Chrome.
There they claim that “A Not Secure label on your website can devastate your business.”:
No evidence is presented for that despite it being a serious claim.
What seems like a clear indication that they are not interested in informing people about what is happening, but selling something is another part of that page which states that using HTTPS will “shows visitors they’re safe with the little green lock in their address bar”:
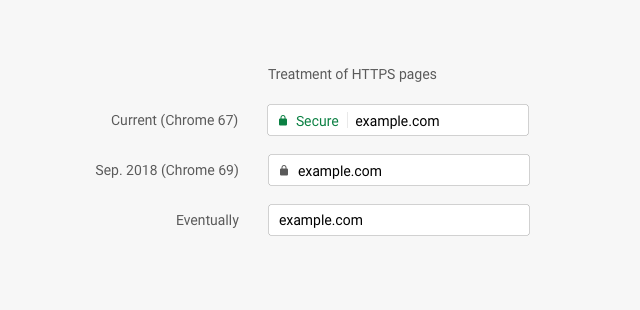
The next HTTPS related change in Chrome, occurring in September, involves it downgrading what is shown for HTTPS pages:
Do They Know What an SSL Certificate Even Is?
Going back to the page for selling SSL certificates there is what is supposed to be an explanation of how a HTTPS connection works, but it seems to have been written by someone that isn’t familiar with it all:
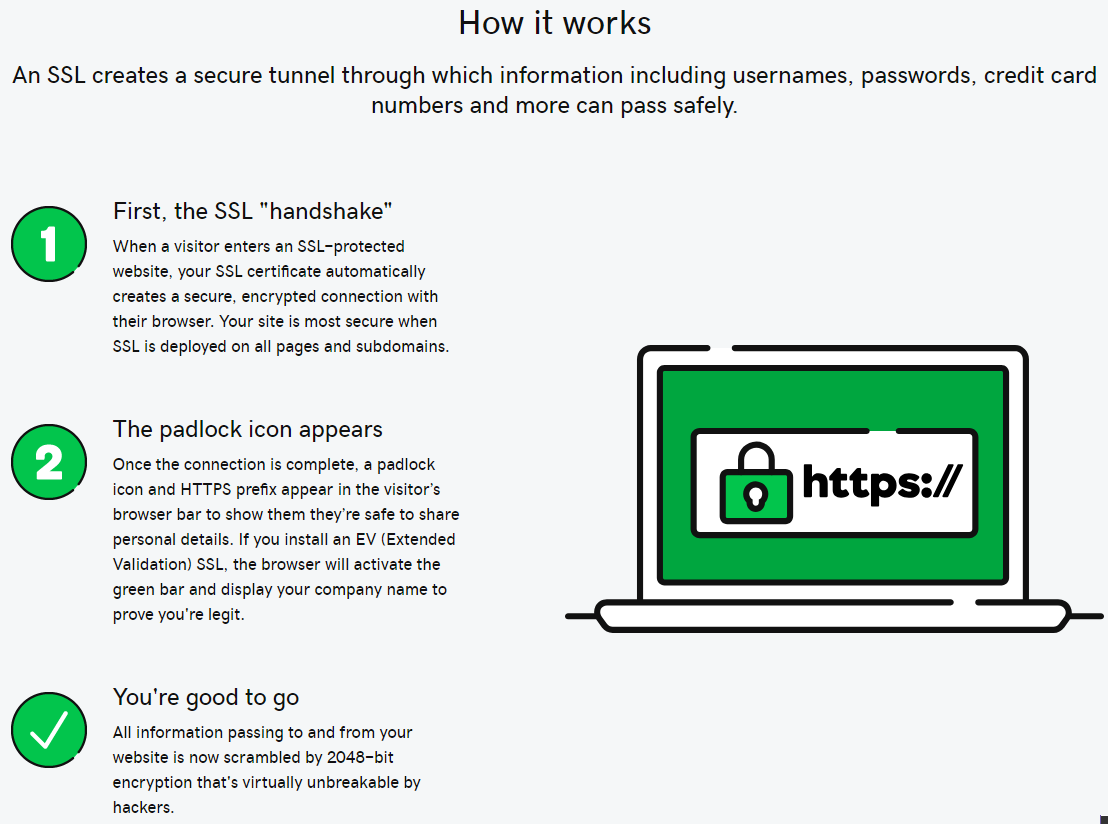
An SSL certificate doesn’t “automatically creates a secure, encrypted connection with their browser”, instead the SSL certificate is just used to validate that a secure connection is being made with the intended website instead or with another party.
Among the other issues with that is that the level encryption is determined by the server and the web browser, not the SSL certificate.
GoDaddy might be able to justify a higher price for an SSL certificate if good customer service was provided, but considering how off the marketing material is, it is hard to believe that their customer service would be well informed about them.