If you deal with security, as we do, it often isn’t hard to tell that companies are taking advantage of their customers, but most of them at least try to hide it to some degree. That isn’t the case with a provider named MalCare. Here, for example, is the interstitial we got shown on their homepage when we recently visited it:
In small text at the bottom it says, “No Thanks, I will let my site be hacked :(“. That makes no sense. A malware scan would show if a website is already hacked, it won’t actually do anything to stop a website from being hacked. Either they don’t understand what they are doing at all, or they have no problem lying to their potential customers.
Getting past that, the first message shown on their homepage was this:
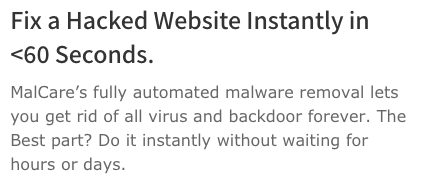
Scrolling down a bit, you get more of the same:
That all sounds great, but it again makes no sense if you have a basic understanding of security. Before we explain why, it’s worth noting that not only doesn’t this make any sense, but MalCare contradicts the claims being made there, right on their website. For example, while the above claims “MalCare’s fully automated malware removal lets you get rid of all virus and backdoor forever”, the pricing page touts one of the features being “Unlimited Automatic Malware Removal”:
If they are removed forever, then you wouldn’t need “unlimited” malware removals.
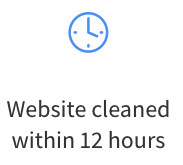
Also, there is a big contradiction in that at the top of their website they highlight an “Emergency Hack Cleanup” service, where they claim the website is cleaned up within 12 hours:
If their instant cleaning service actually properly cleaned up hacked websites, why would anyone need another service that takes up to 12 hours?
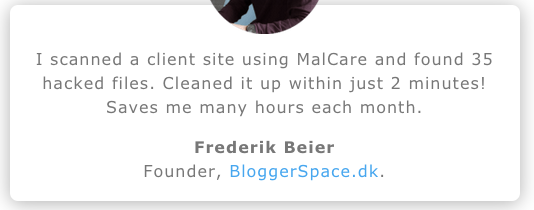
That page also includes this incredible customer testimonial, which ties back to the claims MalCare makes not making sense:
If you are spending hours each month cleaning up malware on your clients’ websites, that means those website are being hacked repeatedly and are still not being properly secured. Who would publicly admit to that? Cleaning up those files doesn’t address the security issue that is leading to them being hacked, so it isn’t surprising that there would continue to be issues.
To properly deal with a hacked website, there are three key components:
- Clean up the hack.
- Get the website secured as possible (which usually involves getting Drupal, contributed modules, and themes on the website up to date).
- Try to determine how the website was hacked and fix that.
The MalCare service doesn’t even claim to address latter two of those, which means that the websites using the service can get hacked over and over. Hence the “unlimited” malware removals.
Based on years of real world experience, things are likely worse than that. What we have found is that automated tools for cleaning up malware, which are actually used by many providers (contrary to how multiple providers claim to be the only ones), don’t produce great results. They both miss plenty of malicious files, but also produce plenty of false positives. That MalCare provides a manual service would indicate that they know this to be the case, while also claiming otherwise. What we have also found repeatedly, is that security companies that don’t try to determine how websites have been hacked miss malicious files that they would have otherwise found. So automated malware removal is quick, but it isn’t good, hence again, why MalCare itself provides a manual cleanup service.
MalCare Thinks Cleaning a Website Doesn’t Involve Making Sure it Works
In looking around more about MalCare we found this odd situation where the reviews of their WordPress plugins are mostly unrelated to the plugin. One of them seems rather informative as to how little you get when you pay for their manual service.
The reviewer wrote this:
I purchased the expensive pro version of this and it did not solve the issue and broke my site.
I bought with confidence because it says on their site :
“Guaranteed 100% WordPress Malware Removal. Without breaking your website.”
and
“Get 3X your money back if we cannot remove your malware.”I have contacted them many times and they refuse to refund my money. It says get 3x your money back but you will not even get it back 1x time
I also asked them to close my account and delete my credit card informations which the also refuse to do.
The substantive part of the response from MalCare is this:
The website was broken because of the changes that you had done to the website via FTP. This detail was mentioned & conveyed by you on the email thread. You had also mentioned that because we were not able to recover the data & make the website look like before, you’re requesting a refund.
But unfortunately, we have no control over plugin & theme data that is on the website which was lost because of the malware attack. At best, we can assist you with cleaning the site which our team has.
We cannot process a refund because our refund policy clearly states that a refund can be processed only if we are unable to clean the website. But in this case, we did clean all the malware from the site.
As a company that has been doing cleanups of hacked WordPress websites for over a decade, we have never left a website broken after a cleanup. We wouldn’t even consider doing that. If data was truly gone, then we couldn’t restore it, obviously, but we would have determined that before starting the process instead of making a promise, we couldn’t keep. We also charge after the work is done, not before, which we have always felt is better a guarantee.
Numbers Never Lie
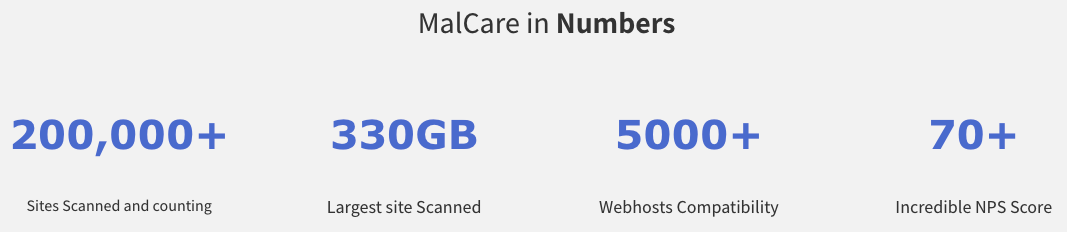
When looking at the websites of services like this one, one thing that is easy to check to see if they look legitimate is the stats they show. Not surprisingly, like the others, they don’t point to any independent testing of their services effectiveness, but they do claim to be compatible with 5,000+ web hosts:
We can safely say they couldn’t even name 5,000 web hosts, much less have they determined if they were compatible with that many.