We frequently have people contacting us for a second opinion on claims from the security company SiteLock that their websites have been hacked. To be able to provide that we ask for the evidence being presented by SiteLock to back that claim up. An important reason for doing that is that SiteLock appears to refer to anything they detect as possibly being an indication of a hack as malware, even if it isn’t malware.
Malware is short for malicious software and can accurately refer to one of two things when it comes to websites. The first being malicious code being served from a website and the second being malicious code located in a website’s files or database.
One reason why they might refer to any indication of a hack as being malware is to make the issue sound more serious than it really is and make you more likely to pay them for some security service. As an example of that, in one instance where we were contacted about a claim of theirs, what they were claiming was “critical” severity malware was just a link to another website. What was even supposed a problem with the link, which was included with a comment on a blog post, wasn’t clear since the domain name of the website being linked wasn’t registered anymore, but saying there is an issue with a link would sound a lot less concerning than “malware”.
Someone that they recently contacted with a claim that their website contained malware, had also been told by the SiteLock representative that called them that Google would “shut down” their website due to the issue. In reality Google doesn’t shut down websites and since the issue wasn’t actually malware they wouldn’t even block access to the website if they had detected the issue.
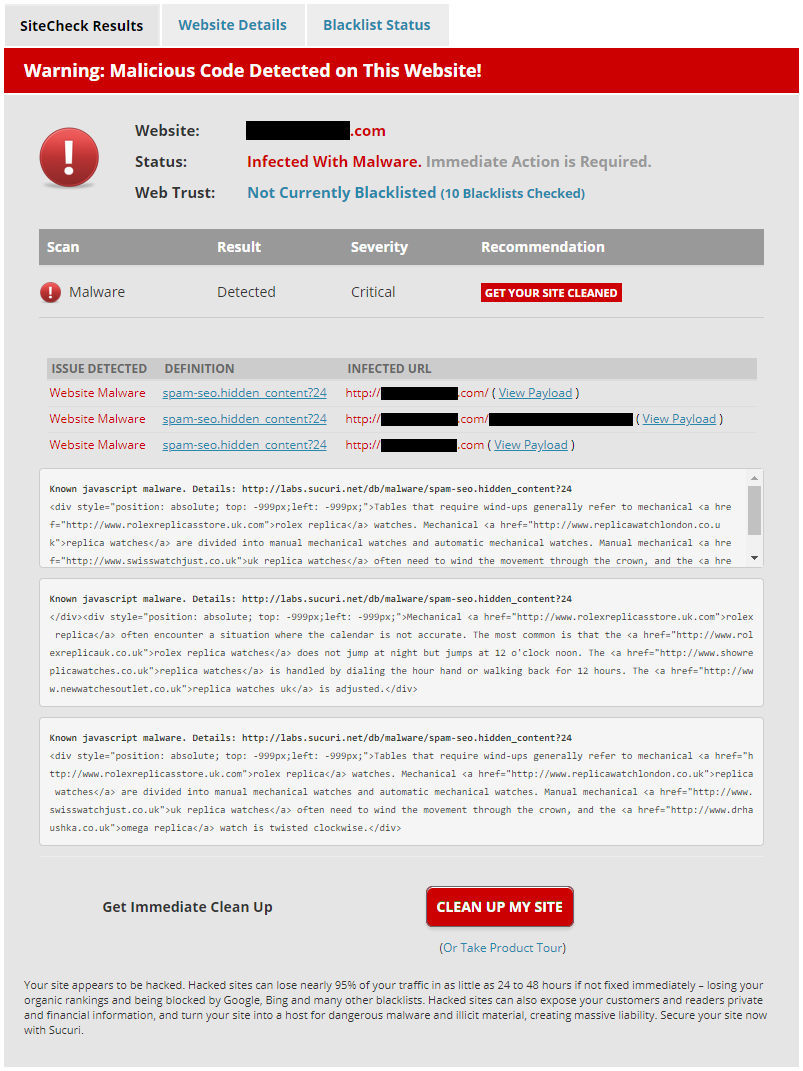
That person had then run the website through the Sucuri SiteCheck scanner, which also claimed the website contained malware. Sucuri also goes the over top in making issues seem as bad as possible to sell their service:
The small text there states:
Your site appears to be hacked. Hacked sites can lose nearly 95% of your traffic in as little as 24 to 48 hours if not fixed immediately – losing your organic rankings and being blocked by Google, Bing and many other blacklists. Hacked sites can also expose your customers and readers private and financial information, and turn your site into a host for dangerous malware and illicit material, creating massive liability. Secure your site now with Sucuri.
What they actual identified there is what we would describe as hidden spammy content, which is a less serious issue than malware. It also didn’t contain any code, JavaScript or otherwise, despite Sucuri labeling it as “Known javascript malware” and stating that “Malicious Code Detected”.
While Google might penalize a website for that hidden spammy content like that, it isn’t going to do any harm to people visiting the website.
If you visit the link they provide for the details of that type of issue, http://labs.sucuri.net/db/malware/spam-seo.hidden_content?24, the description doesn’t mention “malware”, but does mention “hiding spammy content”:
Hiding spammy content (links, spammy texts, etc) on legitimate web pages is a common black hat SEO trick. It helps use existing site pages in black hat SEO schemes while keeping it invisible to site visitors and webmaster.
There are many techniques that help hide certain parts of a web pages. Most of them include either CSS or JavaScript. The simples is placing spammy content inside a div tag with the display:none; style.
Another interesting similarity between those two companies, which seems like it ties in to the overstated impact of the real issue on this website, is that security services provided by both SiteLock and Sucuri don’t seem to be focused on actually securing websites. Instead they seem to be more focused on trying to deal with after effects of the website having been hacked after having left the websites insecure. That all could be an indication the companies don’t have a good understanding of what they claim to have expertise in or that they are just interested in trying to get as much money out of people instead of being focused on improving security.