Last week we looked at the fact that web security company SiteLock’s recent claim of a trending threat had an obvious falsehood in it, which was that a malicious WordPress plugin was a forgery of legitimate plugin despite the supposed legitimate plugin not existing. The rest of their post on the issue lacked evidence to back up their claims and it seemed that the malicious plugin might be rather old and not a new trend. Unfortunately a number of security news source repeated their claims verbatim instead of doing any fact checking (with two of them we left comments on their posts mentioning that the legitimate plugin didn’t exist, but neither of them have approved our comment to show on the posts yet)
Based on that and everything else we have seen from SiteLock isn’t really surprising to see that they made an obviously false claim with their next claimed trend as well.
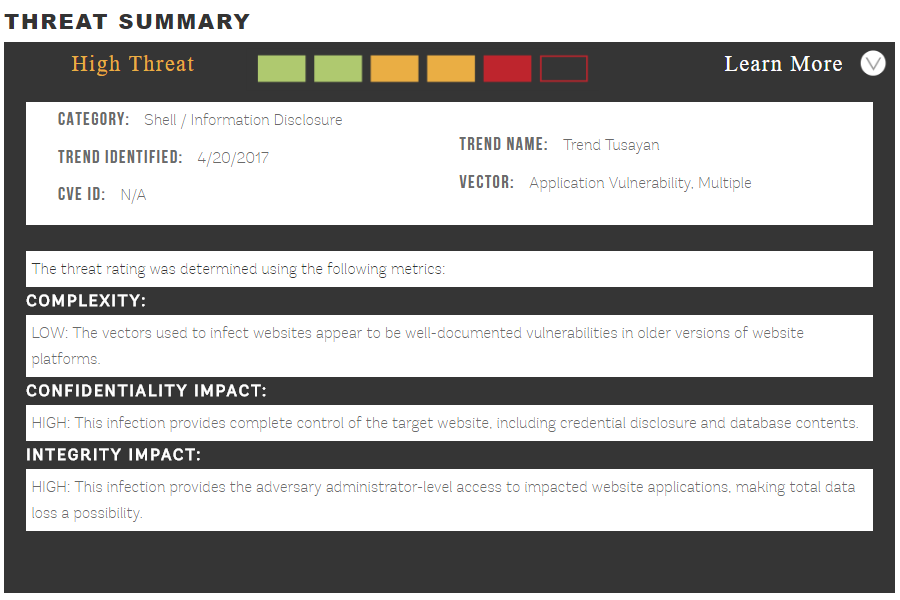
Before you even get to the contents of the post there already is something that looks us to be a good red-flag that the post isn’t something that should be taken seriously, it’s this graphic:
It reminds of the overused breaking news graphics on cable news, which seem to be used for things that don’t seem to qualify far too often.
The main portion of the post is a good example of the poor quality content put out by security companies. Frequently they will dress things up to make something trivial or in some cases made up, seem more serious. In this case with this infographic:
They even give the claimed trend a name (because trying to brand vulnerabilities was not enough).
At the heart of the claimed trending threat is that websites running outdated software can be hacked:
The vectors used to infect websites appear to be well-documented vulnerabilities in older versions of website platforms.
Which isn’t anything new. It is worth noting that SiteLock doesn’t cite any specific vulnerabilities, which would leave us to believe they don’t actual know the source of hacks. We have often found security companies and web hosts will claim that website have been hacked through outdated software based on zero evidence (in some cases we have seen this claimed when the software of the website was actually being kept up to date). From everything we have seen SiteLock usually doesn’t determine how websites are hacked when cleaning them up, despite that being one three main pieces of doing that correctly, which increases the chances that they don’t actually know in this instance either.
If there was something worth noting here it relates to the possible compromise of cPanel login credentials, not CMS credentials, through the hack. SiteLock make no direct mention of that, only mentioning to change the cPanel password if using that, which is another indication that SiteLock doesn’t have much security expertise and experience.
SiteLock Doesn’t Suggest Taking the Action to Prevent the Real Threat
The last section the post is what seems to be the real point of their post, to promote one of their products, which doesn’t actually fix the claimed root of this, which is outdated and vulnerable software. It starts this way:
Here’s what you need to do
As this trend both provides administrator-level control over the target website environment as well as publicly discloses credentials, action must be taken to counter both threats.
Since again, the important threat is the vulnerability being exploited to allow the hacker access to the website in the first place, not what could be done if it is exploited since that can be stopped from happening, you would expect the first action they suggest be to make sure the software on a website up to date, instead it is:
- Run a malware scan to locate the presence of any shell files. (see: SiteLock Malware Scanners)
In fact updating the software on the website isn’t listed at all. Do they want websites to remain vulnerable to being hacked? It is worth noting that we are not aware of any SiteLock ongoing security services that include them keeping a website’s software up to date (not surprisingly we have seen numerous instances of their customers using those services getting hacked.)
False Claim
Finally let’s look at the false claim, which is this:
The code within the shell used to gain the initial foothold is currently listed in the SiteLock malware database, but does not appear to be widely recognized as a threat by many website security vendors at this time. You may use the code snippet below to manually add the shell to your security mechanisms.
Looking at the screenshot they provided of the backdoor script, there is a line code that would immediately stick out to anyone that regularly deals with hacked websites:
That would be this part “$default_action = ‘filesman'”. Looking back it looks like backdoor scripts with that line of code have been in existence at least since 2010.
The idea that the code wouldn’t be “widely recognized as a threat by many website security vendors at this time” indicates SiteLock is clueless, is lying, or thinks the rest of web security industry is even worse than them (which might explain their laughable claim to be the global leaders in website security). None of those possibilities is something that should be able to be said about a security company.
A Better Alternative to SiteLock For Cleaning Up a Hacked Website
If your web host is pushing you to hire SiteLock to clean up a hacked website, we provide a better alternative, where we actually properly clean up the website.