In the past few days they have been two reports of a vulnerability in WordPress 3.2.1. In looking into these we found that the claims to be supported by false information and no evidence of a vulnerability in WordPress 3.2.1 was presented. A number of news organization including SC Magazine, The Register, and PC World repeated the claims without bothering to check the information for themselves. We still would recommend that anyone running an outdated version of WordPress upgrade to version 3.3.1 (which one of the security companies making the claims hasn’t done itself) and to make sure you keep all the software on your websites up to date at all times.
Websense
The first claim is by the Principal Security Researcher at Websense. In their post it is stated that “Based on my analysis, the site was compromised because it was running an old version of WordPress (3.2.1) that is vulnerable to publicly available exploits [1] [2]”. Looking at the exploit reports they are for two WordPress plugins not for WordPress itself, so the analysis is fundamentally wrong.
If those exploits actually work (we didn’t test them) then it wouldn’t matter what version of WordPress you were running only if you were running the vulnerable version of the plugins. We checked a few of the sample websites they listed and it did not appear that they were running either of those plugins.
Their other evidence that the exploit was something related to WordPress 3.2.1 is the claim that all of the website were running that version of WordPress. If this is true (the sample list of 17 websites they provided were all recently running WordPress 3.2.1) it doesn’t necessarily mean that the hack was related to something in WordPress 3.2.1 or WordPress at all.
One likely possibility is that they are all running some other outdated software, maybe a WordPress plugin, that contain a vulnerability. Websites running an outdated version of WordPress are more likely to have not kept other software on the websites up to date as well.
WordPress and WordPress 3.2.1 run on many websites so it also could be that some other type of exploit, like compromised FTP credentials or hacked hosting providers, could be the source. We know that sometimes hackers specifically target WordPress installations when using non-WordPress related exploits, something that Websense has in the past falsely claimed as being an exploit of WordPress itself.
M86 Security Labs
The second claim comes from M86 Security Labs. In their post they state that “A few days ago, hundreds of websites, based on WordPress 3.2.1, were compromised. ” We checked what version of WordPress the sample list of 33 website they included in their post were running. We found that many of them were not running WordPress 3.2.1. Here is the breakdown:
3.3.1: 7
3.3: 2
3.2.1: 8
3.2: 1
3.1.1: 1
3.0.3: 2
3.0.1: 1
They were also 11 websites that were inaccessible at the time we checked. Of 22 we could check, less than half were running 3.2.1. Nine were running newer versions and five were running older versions. It possible that the ones running newer versions were upgraded after they were exploited, but it makes no sense that websites running older versions were running 3.2.1 at the time of the exploit. This clearly indicates that the websites were not all running WordPress 3.2.1 as claimed and that exploit is not something specific to 3.2.1. It is possible that it could be related to something that existed in 3.2.1 and below, but there is no evidence provided by them to support that.
If you visit the M86 Security Labs Blog with our Meta Generator Version Check extension (available for Firefox and Chrome) you would get an alert the blog is running an outdated version of WordPress, 3.1.3.
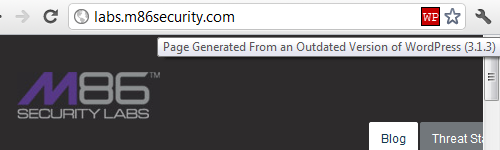 If they really believe there is a vulnerability in outdated versions of WordPress why are they running an outdated version on their own blog?
If they really believe there is a vulnerability in outdated versions of WordPress why are they running an outdated version on their own blog?