On most days we now have multiple people contacting us in regards to claims made by SiteLock and their web hosting partners about the security of their websites. Those contacts broadly fall into to two categories these days.
The first involves websites that SiteLock and their hosting partners are claiming are hacked, which are in fact hacked, but seemingly due to their reputation and shady sales tactics, the websites’ owners believes that the websites are not hacked. In some cases we even are contacted by people claiming that SiteLock or their web host has hacked their website, though those claims have appeared to be completely baseless (we have seen zero evidence ever that SiteLock has hacked any websites).
The second category largely involves SiteLock and their web hosting partners making seemingly baseless claims that websites contain some vulnerability, are at high likelihood of being hacked, or have some other security issue. A recent source of many of those claims has been something referred to as the SiteLock Risk Assessment, which is supposed to provide a score of how likely a website is to be hacked based on “predictive model that analyses over 500 variables “, but the scores appear to be unconnected to reality.
The combination of those situations is not just bad for the people having to deal with the claims made by SiteLock and or their web host, but also for the general public since websites that are really hacked are not being seen as having the serious issue they have, due in part to the false claims also being made.
A recent example of the latter category stood out to us as a good example of the type of activity that has caused SiteLock to earn a reputation as scammers.
We were recently contacted by someone that had multiple calls and emails from SiteLock claiming their website contained malware. Below is one of the emails that was sent by SiteLock about this supposed issue:
Dear SiteLock Customer,
My name is [redacted] and I’m a Security Consultant here at SiteLock Website Security.We are reaching out to you because one or more of the domains you own has malware on it and this issue needs to be resolved. As your website security provider you Do Not have the appropriate level of security to remedy/ remove and prevent these issues.
I’ve attempted to leave a message or left a message on the number in our records as well.
Contact me immediately and directly. We are able to assist you. [redacted] // [redacted]Cheers,
Worth noting here is that SiteLock’s usage of “Security Consultant” is in fact a euphemism for a commissioned sales person, who likely doesn’t have any background in security.
When we were contacted about this, we asked if there had been any evidence provided to back up the claim that the website contained malware. One reason for doing that is that SiteLock labels all sorts of things that are not malware as being malware, so that makes providing a second opinion in many instances very difficult because the claimed issue could be one of many things.
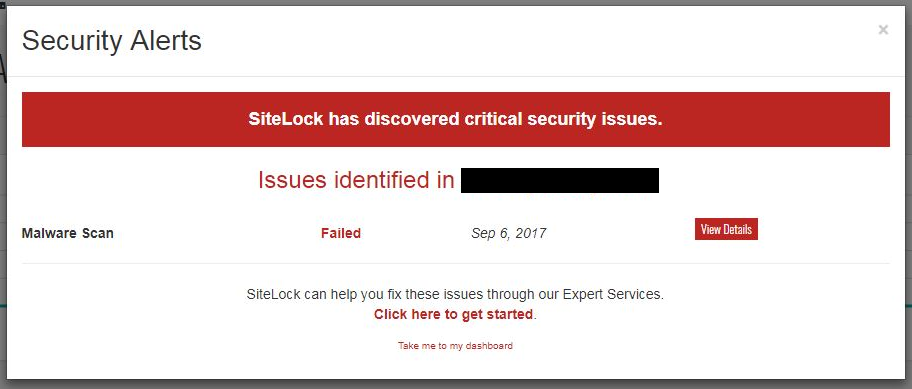
The website’s owner had not been provided any yet and after SiteLock was asked for evidence, a couple of screenshots were provided. The first showed the following alert box:
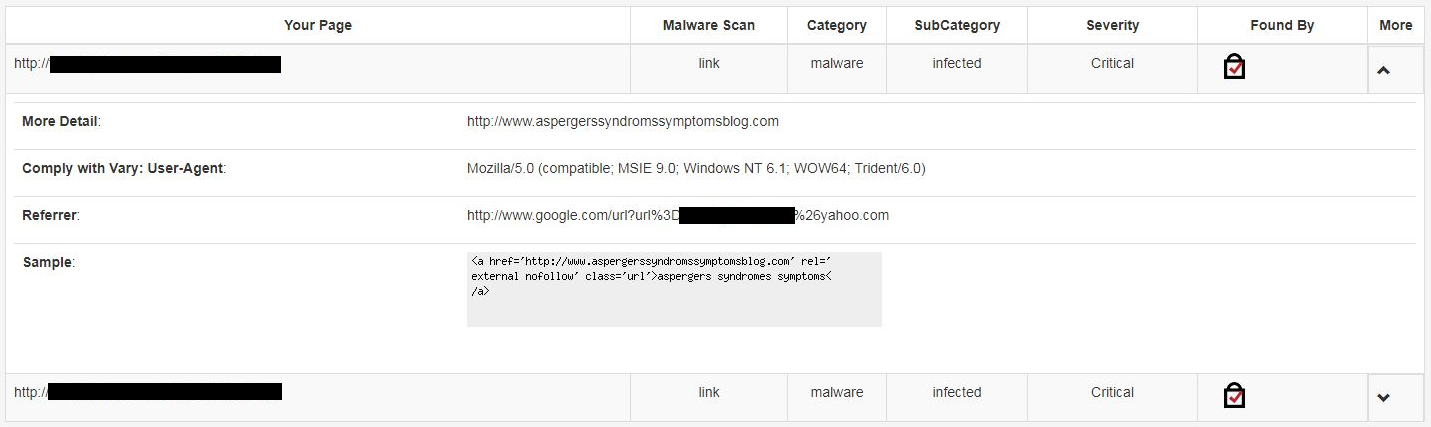
What the “critical security issues” is supposed to be is shown in the second screenshot:
The most relevant portion is shown here:
So by malware on the website and “critical security issue” they really meant there was a link to another website. The link in question wasn’t something that was placed on the website as part of a hack of the website, instead the URL was the website provided with a comment on a post from 7 years before. So the claim didn’t seem at all accurate and the repeated contact by SiteLock seemed unreasonable, but it gets worse. We expected that at least the linked to domain, aspergerssyndromsymptomsblog, would contain something malicious, why else would they be claiming it was malware? But instead we found that the domain name isn’t even registered anymore. So a link from a comment to an unregistered domain caused SiteLock to claim a website contained malware.
The positivity and high energy makes me want come to work each day. We provide valuable products that help business owners succeed, without them having to worry about security issues. We also have great perks here, including free breakfast on Mondays and lunch on Fridays, an on-site gym and cafe, and an employee game room. I feel right at home!
In reality it appears that SiteLock is actually causing people to worry about security issues that don’t even exist and then trying to sell them solutions to protect them from non-existent issues.