Yesterday we were contacted by someone looking for second opinion as to whether the web security company SiteLock’s claim that their website contained malware was true. The website’s owner believed that their web host BlueHost and SiteLock might be trying to scam them.
In the case of this website it wasn’t hard to determine that the website was hacked, as this is what was shown on the homepage:
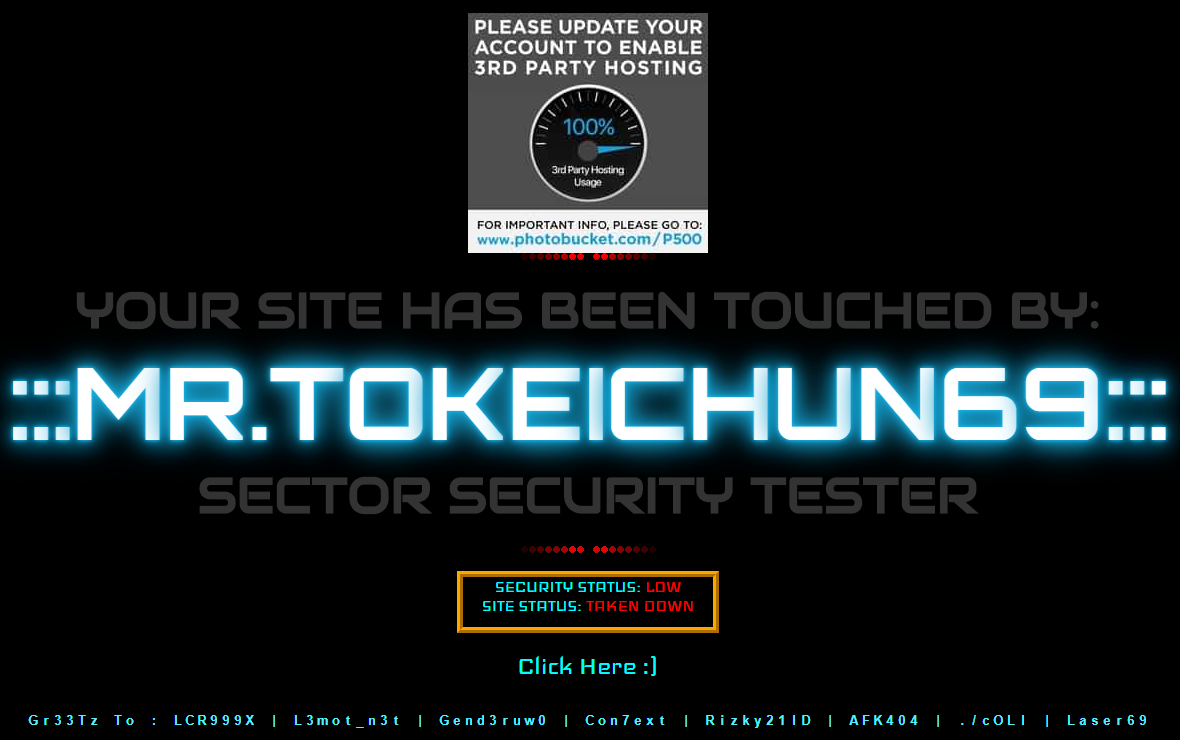
That type of hack is referred to as a defacement hack.
By malware, that may have been what SiteLock was referring to because as we found while previously giving someone a second opinion, for some reason SiteLock labels evidence of a defacement hack as malware (that seems to be a general issue, as they also labeled a spam link that way as well).
After we let website’s owner know that unfortunately the website was hacked, they responded that they felt it was an inside job. We didn’t believe that to be the case, but instead of just saying that was unlikely, we wanted to be able to provide more concrete evidence.
One way to do that would be to find some other websites hit with same defacement that were not hosted with the same web hosting company or another one partnered with SiteLock. When we did a search on Google for “Mr.ToKeiChun69” the first result was a page documenting defacements by Mr.ToKeiChun69 on the web site Zone-H.org, which documents defacements of websites.
In looking at some of the websites that had been defaced by Mr.ToKeiChun69 we found that they all were hosted by web hosting brands owned by the Endurance International Group (EIG). Their brands include BlueHost, as well as A Small Orange, FatCow, HostGator, iPage, IPOWER, JustHost, and quite a few others. SiteLock has a “security partnership” with EIG where SiteLock pays EIG a majority of the fees from services sold through the partnership. The majority owners of SiteLock also run EIG.
While that might lead some to see the worst case, that this was inside job, for us it didn’t. But it did seem rather odd that all the websites would be at one web hosting company and that was possibly an indication that the company has some security problem.
To better understand if there was really a correlation between the web hosting provider and these defacements we did a more thorough check of where the defaced websites were hosted. We checked the first ten websites listed on the 1st, 11th, 21st, 31st, and 41st page of results for this defacement on Zone-H.org. That checked websites that are dated on there as far back as June 29.
Below are the results. We have listed each domain name, the IP address it currently is hosted on, and finally the ISP listed for that IP address or the web host. The ISP Websitewelcome.com is connected to HostGator and Unified Layer is connected to BlueHost, though the websites might be hosted with other EIG brands.
Page 1
- endblameshameguilt.com: 192.254.236.84 (Websitewelcome.com)
- acimfordummies.org: 192.254.236.84 (Websitewelcome.com)
- wakechild.com: 192.254.236.84 (Websitewelcome.com)
- tena-frank.com: 192.254.236.78 (Websitewelcome.com)
- acourseinmiraclesfordummies.com: 192.254.236.84 (Websitewelcome.com)
- decodingacim.com: 192.254.236.84 (Websitewelcome.com)
- endblameshameguiltgame.com: 192.254.236.84 (Websitewelcome.com)
- toddtylermusic.com: 192.254.236.80 (Websitewelcome.com)
- lachildrensridingcenter.com: 192.254.236.8 (Websitewelcome.com)
- topsportscamcorders.com: 192.254.236.8 (Websitewelcome.com)
Page 11
- iphonenstuff.com: 192.254.236.82 (Websitewelcome.com)
- sneakerpicks.com: 192.254.236.82 (Websitewelcome.com)
- dalmatianadvice.com: 192.254.236.82 (Websitewelcome.com)
- subscribesave.com: 192.254.236.82 (Websitewelcome.com)
- helpmebuilda.com: 192.254.236.82 (Websitewelcome.com)
- bestboatplans.com: 192.254.236.82 (Websitewelcome.com)
- spelbonusar.com: 192.254.236.82 (Websitewelcome.com)
- gamingnshit.com: 192.254.236.82 (Websitewelcome.com)
- marenart.com.au: 192.254.236.82 (Websitewelcome.com)
- retailstartupbookinabox.com: 192.254.236.82 (Websitewelcome.com)
Page 21
- www.blackandwhitesecurityltd.com: 192.254.232.90 (Websitewelcome.com)
- dallasgayboys.com: 192.254.232.86 (Websitewelcome.com)
- untieeecs.com: 192.254.232.86 (Websitewelcome.com)
- jonathanjoyner.com: 192.254.232.86 (Websitewelcome.com)
- www.smcntx.com: 192.254.232.86 (Websitewelcome.com)
- www.culinairteamzeeland.nl: 192.254.232.90 (Websitewelcome.com)
- strandvakantieman.nl: 192.254.232.90 (Websitewelcome.com)
- napers.nl: 192.254.232.90 (Websitewelcome.com)
- www.camping-renesse.nl: 192.254.232.90 (Websitewelcome.com)
- www.campingdebrem.nl: 192.254.232.90 (Websitewelcome.com)
Page 31
- 81tagorelane.com: 50.87.147.75 (Unified Layer)
- skies39-newlaunch.com: 50.87.147.75 (Unified Layer)
- newlaunch-gshplaza.com: 50.87.147.75 (Unified Layer)
- 3dinvisibilitycloak.net: 192.232.251.55 (Websitewelcome.com)
- professional-liability-insurance.net: 192.232.251.55 (Websitewelcome.com)
- lyynx.net: 192.232.251.55 (Websitewelcome.com)
- aksolution.net: 192.232.251.55 (Websitewelcome.com)
- krilloils.org: 192.232.251.55 (Websitewelcome.com)
- 3dinvisibility.org: 192.232.251.55 (Websitewelcome.com)
- ellipticalmachineshelp.com: 192.232.251.55 (Websitewelcome.com)
Page 41
- topwebber.com: 192.185.21.208 (Websitewelcome.com)
- yoholly.info: 192.185.21.208 (Websitewelcome.com)
- myironsuit.com: 192.185.21.208 (Websitewelcome.com)
- laptoplifestylecafe.com: 192.185.21.208 (Websitewelcome.com)
- bellyfatcombat.net: 192.185.21.208 (Websitewelcome.com)
- herbzombie.com: 192.185.21.208 (Websitewelcome.com)
- biggerbuttshortcuts.com: 192.185.21.208 (Websitewelcome.com)
- blowtalk.com: 192.185.21.208 (Websitewelcome.com)
- waisttraineraustraliaco.com: 66.198.240.58 (A2 Hosting)
- besthairextensions.co.nz: 192.185.44.88 (Websitewelcome.com)
With 49 of the 50 websites currently being hosted with EIG that would certainly seem to point to there is some correlation between the web host and the hackings. As with something that doesn’t have a connection to a web host, you would expect to see a fair amount of different web hosts showing up with that many websites.
So what about the one website that isn’t currently hosted with EIG? It turns out it was hosted with them at the time it was defaced. The IP address of the website on June 29 according to Zone-H.org was 192.185.44.88, which is one connected to HostGator. The records for the domain name were changed on July 4, which is probably when the web hosting was changed.
We don’t know what the cause of this is. It could be that the person or persons behind the Mr.ToKeiChun69 defacements is only targeting EIG hosted websites, has been unsuccessful in targeting websites at other web hosts, or only notifying Zone-H.org of websites hosted with EIG. What would seem more likely is that they are taking advantage of some security issue in EIG’s systems.
To be clear we don’t think that this is an inside job.
We notified the person that contacted us about the correlation, which they hopefully will pass along to BlueHost.