One of the more recent activities from the web security SiteLock that seem like it could be classified as a scam, is a score, from “low” to “medium” to “high”, that is supposed to indicate how likely a website is to be hacked.
We first ran across it when a Forbes contributor wrote about how they were told that their website, which consists of a “static HTML page with a few images and a few locally hosted CSS, font and JavaScript files”, was at “medium” risk based on this score. When the author of the article raised question about this, SiteLock couldn’t even explain a way that the website could be hacked that was considered by their score despite claiming it was at “medium” risk of that happening. Another element that makes this seem like a scam was that SiteLock provided supposed percentages of the risk that that got to “medium” risk, which don’t seem believable. Most of the risk, 64%, came from the “Site size and the number of distinct components”, despite the website having only one page and no components that seem like they could have lead to the website being exploited.
With SiteLock claiming that website was at “medium” risk, we wondered what it would take for SiteLock to claim is at “high” risk. A couple weeks later we got the answer, when we were contacted by someone that had been notified that their website was at “high” risk based on the scoring. So what kind of website is at “high” risk? One that only contained static HTML pages, but it did have multiple pages, so maybe that is enough for them to make that claim.
The question that then left us with was what it would take for a website to receive a “low” risk score. The answer it seems, based on a recent tweet we ran across, is for a website where the domain name that isn’t even registered:
@SiteLock You email me security reports for a non-existent website. #LOL #FAIL pic.twitter.com/XAs8rwhjrC
— Brett (@BrettJo02676296) September 21, 2017
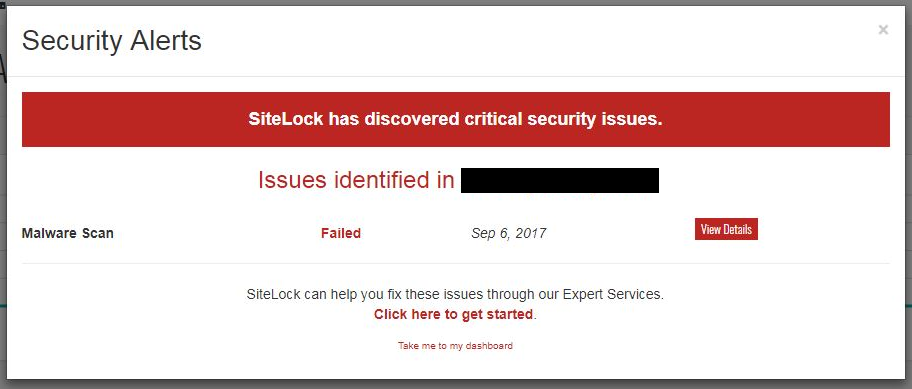
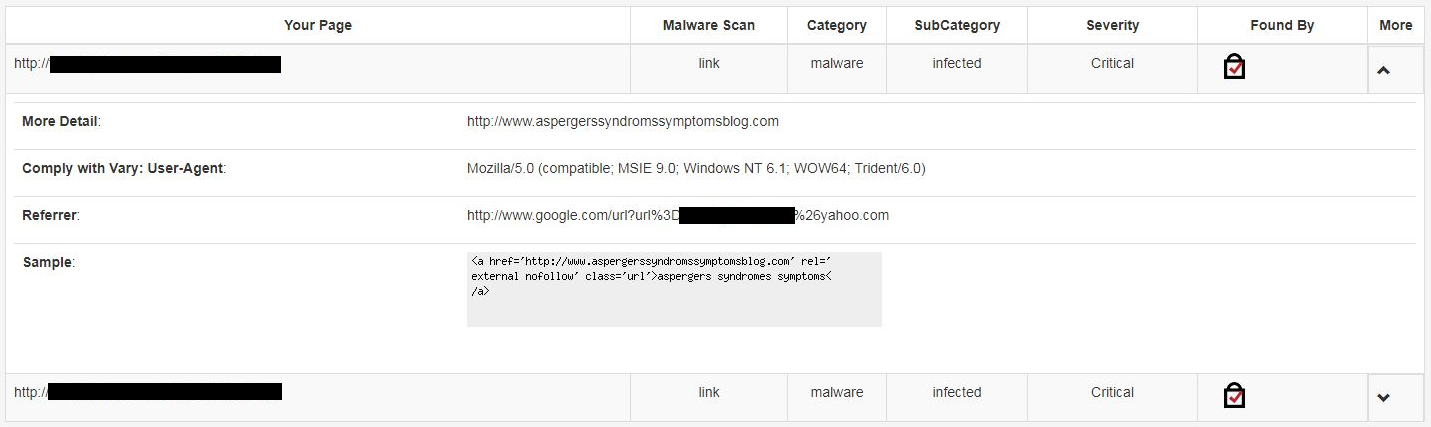
This isn’t the only recent issue we have seen with SiteLock and an unregistered domain name, as several weeks ago we discussed a claim from SiteLock that a website contained “critical” severity malware due to a link to an unregistered domain name.
In looking for other instances of the “SiteLock Platform Digest” show in that tweet, we ran across someone that had received it unsolicited and SiteLock tried to claim that it was sent due to a web host, despite the web host having nothing to do with SiteLock.