We were recently contacted by Comodo about some sort of a partnership with their cWatch service. From the homepage of that service, things immediately seemed questionable. They are offering “Free Instant Malware Removal”:
To properly remove malware or some other hacking issue, you can’t do it instantly. If you do it properly it will take some time and it will cost somebody money, so at best they were offering this as a loss leader to sell their other service and more likely they were not doing it right (like it is true of so many companies based on how many people come to us to re-clean websites). The instant claim would seem to indicate that they are using an automated method to do that, which based on plenty of experience seeing the poor results of that, it doesn’t work all that well. Why they would think we would partner with them when they are at best offering to do what we do for free, we didn’t understand.
Looking a little further, things didn’t seem better. They one post on their blog, How to Clean a Hacked Joomla! Site, which is more an ad for their services than any actual information on the subject.
What will be relevant in a second is that at the end of the post it says:
Prevention is better than cure.
One of the preventative measures they list before that is:
- Update the Joomla! software and all its components including core files and extensions.
From there we got to a post on blog of the CEO of Comodo, Melih Abdulhayoglu, Free Hacked Website Repair & Malware Removal. Before we get to the details of that, what is worth noting is that this blog is running an outdated and insecure version of WordPress as can be seen from the source code of the page:
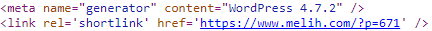
That version was superseded by version 4.7.3 on March 6, 2017. So the WordPress version is eight months out of date. That shouldn’t be the case because normally the automatic background updates feature of WordPress would have updated it shortly after the new version was released. So either that feature has been disabled or there is some incompatibility between the feature and hosting environment of the website. If it was the latter that would be something that Comodo could work with WordPress to fix it for everyone.
What continues to stun us is that we keep finding securing companies that are running outdated and insecure versions of WordPress despite the automatic updates that manages to work for the average website and the fact that security companies should know better than anyone else about the need to keep software updated. In just the last year we have already mentioned on this blog that we have run into this same situation with the following security companies: Checkmarx, Cloudbric, Trend Micro (who got hacked because of it), and PacketSled. We ran into all of those without going out and looking for companies with this situation, so they are likely to be more than that.
Version 4.7.3 was a security update. So were versions 4.7.5, 4.7.6, and 4.7.7.
Also from the source code you can see that website is running version 4.2.8 of the plugin Captcha:

That version is also eight months out of date and contains a reflected cross-site scripting (XSS) vulnerability that we and at least two other entities discovered. That is a type of vulnerability that isn’t likely to be exploited on the average website, but seem like a more likely target in the case of a security company run by people that don’t seem to care much about security. If Comodo was using our Plugin Vulnerabilities service they would have been alerted to that fact back in April.
The outdated WordPress install is also an issue on the Comodo blog:

You also have to wonder if they use their own service or if works at all, as one of the features is “Daily Malware & Vulnerability Scan”, which should being warning about those vulnerabilities:

Seeing as Comodo doesn’t take their own advice on keeping software up to date, they seem like a good example of terrible state of the security industry. If you look at controversies section of the Wikipedia page about the company there have been a lot of other problems with the company.
Another item that seems worth noting for its questionable nature is this row of major company logos on the homepage, which isn’t explained but we would guess that Comodo would want you to assume they use the service (which at least most of them probably are not):

Improper Cleanups
The CEO of the company is also listed as its “Chief Security Architect” and claims to be an “Internet security expert”.
Getting back to the post he wrote, it is cringe worthy, as it starts:
We are in web sites where we were in 90s for computers!
It was a new concept to protect your PC with antivirus products in the 90s. Now its the norm.
Websites and webhosting is where computers were in 90s…still unprotected….still getting hacked and infected….
PC’s are still getting hacked and infected despite antivirus software. The reason that websites get hacked and infected isn’t because they don’t have antivirus software, it is because of various security issues. The solution is to fix those, not to try to poorly detect attempts to exploit those.
One of the ways websites get hacked is when login credentials for the website are compromised on a PC through malware on it, which still happens despite antivirus being “the norm”.
Next up is this:
Today there is a healthy market of selling “malware cleaning” or “hack repair” for website owners. At a hefty price!
This is not the solution! The malware will come back no matter how many times you clean it.
The business model of “Profiting from Website Malware Cleaning” must STOP!
The need for cleaning malware from your website is not going away, but “Profiting from it” is!
If you properly clean up malware, as we do, it doesn’t come back, because part of proper cleanup is figuring how the website got hacked and fixing that. If a new vulnerability is being exploited then the person doing a proper cleanup can then work with the vulnerable solution to try to get that fixed to prevent others website from getting hacked.
Based on that it isn’t surprising that Comodo can offer their service for free, since they are explicitly cutting corners, and you really are getting what you pay for there.
Then a few lines down, the post explains why they are providing free cleanups:
We build innovation to keep you safe, protect you from hacks and malware. The very people who need our Protection is the very people who are hacked and have malware on their websites.
So, by cleaning their site for Free, we hope to gain their trust so that when they choose to protect their site, assumption is that they will, having gone thru the experience of having your site hacked, choose us.
And there is more reason why they should be choosing us. Because there simply is no other technology that can deliver what we can.
We have the world’s very first Website Protection that has a full blown SIEM, Managed WAF, CSOC (Comodo Security Operation Center) staffed by amazing security professionals available instantly 24/7/365 and running on a CDN!
Don’t even think about comparing this amazing technology to legacy “malware scanning” tools out there who are charging website owners an arm and a leg to remove malware.
There simply is no comparison in terms of what CWatch technology can do vs what’s out there!
What you will notice there is that no evidence is provided that their service is effective at all. Offering free cleanups doesn’t mean they can effectively protect websites from being hacked, especially when you don’t do that properly. But they are not alone in this, we have yet to see any company providing such a service like theirs (and there are plenty of them) that provides evidence, much less evidence from independent testing, that they are effective at protecting websites (we did recently run across a security company admitting that they lie when promoting their product with an unqualified statement that it “stops you from getting hacked“).
We have had plenty of people that come to us after having used a service like Comodo’s that ended up failing to protect the website, so without evidence from independent testing that proves that a service is effective we would recommend you avoid it. Instead if you make sure you are doing the basics you are unlikely to be hacked. One of those basics is keeping your software up to date, which Comodo has failed to do with their WordPress installs on the CEO’s blog and their main blog. Why would you possibly trust your security to a company that doesn’t manage to do the basics themselves?
Also notable, is that they are saying you shouldn’t compare them to others, that is probably because as we already mentioned there are plenty of services just like theirs. Humorously one of the thing they tout that they are first to have is “CSOC (Comodo Security Operation Center)”, why would another company have a Comodo branded part of their service?
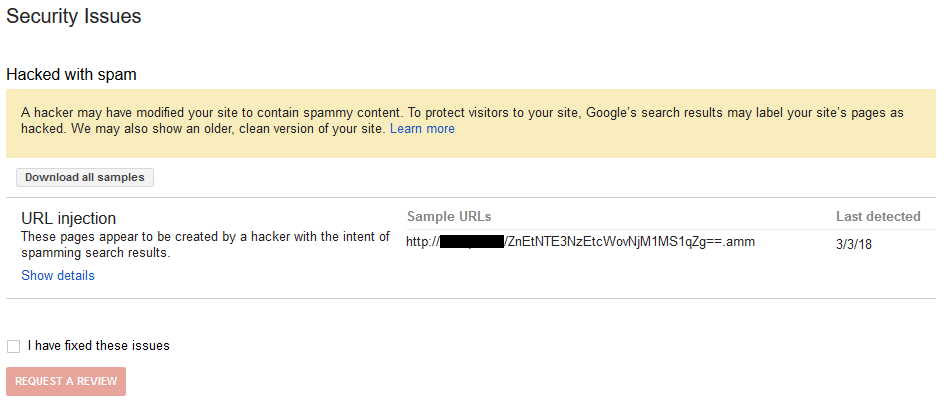 Using the Fetch as Google tool in the Search Console showed that the URL they claimed the issue had been detected on didn’t exist (since the code that generated it was no longer on the website):
Using the Fetch as Google tool in the Search Console showed that the URL they claimed the issue had been detected on didn’t exist (since the code that generated it was no longer on the website):